Contents:
We are witnessing a rise in ransomware attacks, as more and more companies are becoming victims to malicious actors. The Tyler Technology Ransomware attack is one of the most important attacks that happened in the past years as Tyler Technologies, Inc. represents the largest provider of software to the United States public sector.
Ransomware is a type of malware (malicious software) that encrypts all the data on a PC or mobile device, blocking the data owner’s access to it. After the infection happens, the victim receives a message that tells him/her that a certain amount of money must be paid (usually in Bitcoins) in order to get the decryption key. Usually, there is also a time limit for the ransom to be paid. There is no guarantee that if the victim pays the ransom, he/she will get the decryption key. The most reliable solution is to back up your data in at least 3 different places (for redundancy) and keep those backups up to date, so you don’t lose important progress.
The Tyler Technology Ransomware Attack
At the end of September 2020, the company disclosed the fact that it suffered a ransomware attack with its customers apparently finding suspicious logins and previously unseen remote access tools on their networks.
On September 23, 2020, Tyler Technologies experienced a security incident involving unauthorized access to our internal phone and information technology systems by an unknown third party. We treated this matter with the highest priority and enlisted independent IT experts to assist with our containment, remediation, and investigatory efforts. We implemented targeted monitoring to supplement the monitoring systems we already had in place and have been securely restoring affected equipment. We also notified law enforcement, and we have been actively cooperating with them.
The Tyler Technologies ransomware attack happened on September 23 when the threat actors breached the network of the company and managed to deploy the malware.
In response, the company acted quickly and notified law enforcement, whilst also hiring a forensics firm to investigate the incident and discover the extent of the situation.
Soon after the incident, the company representatives declared that the attack only impacted the internal network and phone systems of the company. It seems like the attack managed to cripple the company’s website, email, and phone systems, but fortunately did not appear to spread to any customer systems.
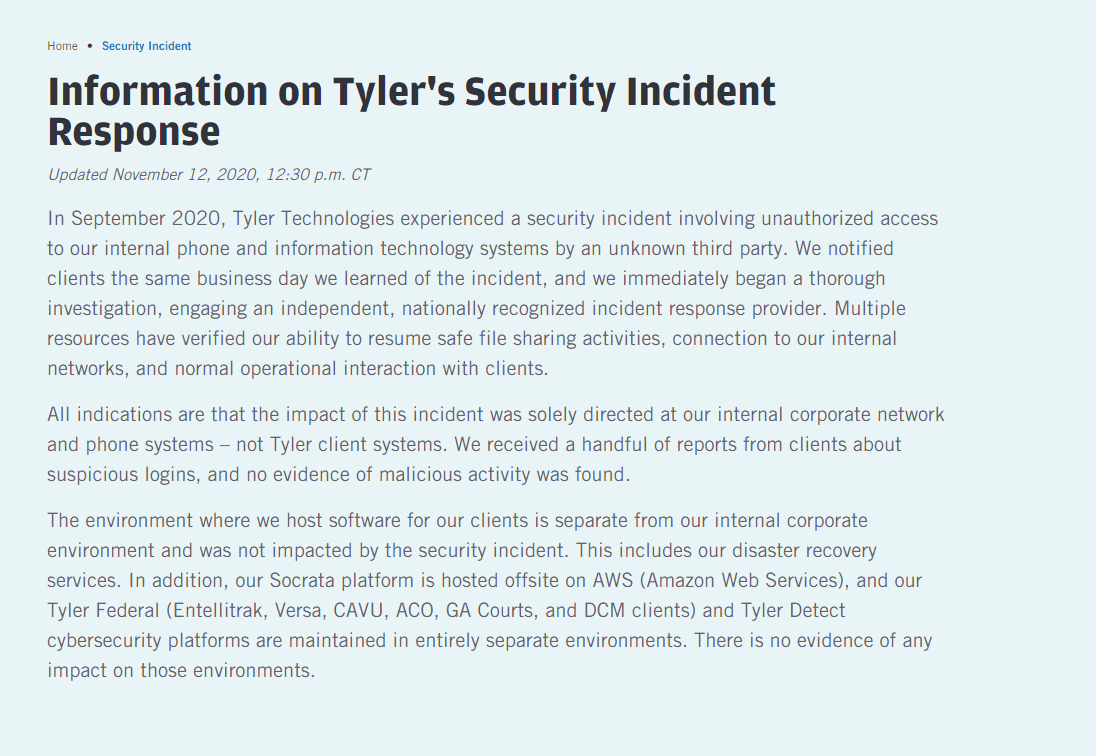
Very soon after the intrusion, Tyler turned its website into an information portal for news about the attack. After two and a half weeks, and frequent updates, the company said it appears the spread of ransomware was contained to its internal systems only, meaning it did not hit any of the software solutions it has deployed into state or federal government.
Who Was Behind the Attack?
The company did not disclose who was behind the attack but, reports circulating online believe that the company was infected with the RansomExx ransomware.
RansomEXX is a human-operated ransomware operation as the attackers manually infect the systems after gaining access to the target network.
RansomEXX is the same ransomware that got employed in a cyberattack on the Texas Department of Transportation, and also towards the systems of the IPG Photonics high-performance laser developer.
The Ransomware Was Paid
It seems that Tyler Technologies paid a ransom of an unspecified amount to receive the decryption key and recover encrypted files.
According to the news publication BleepingComputer:
When the ransomware encrypted Tyler Technologies’ files, they appended an extension similar to ‘.tylertech911-f1e1a2ac.
To prove that the decryptor was valid, BleepingComputer was able to decrypt encrypted files [1, 2] uploaded to VirusTotal at the time of the ransomware attack.
It is important to note that many school districts, court systems, and local and statement governments in the United States are using the Tyler Technologies software, this meaning that the disclosure of data stolen in the ransomware attack could have serious consequences, and for this specific reason, the company decided to pay the ransom.
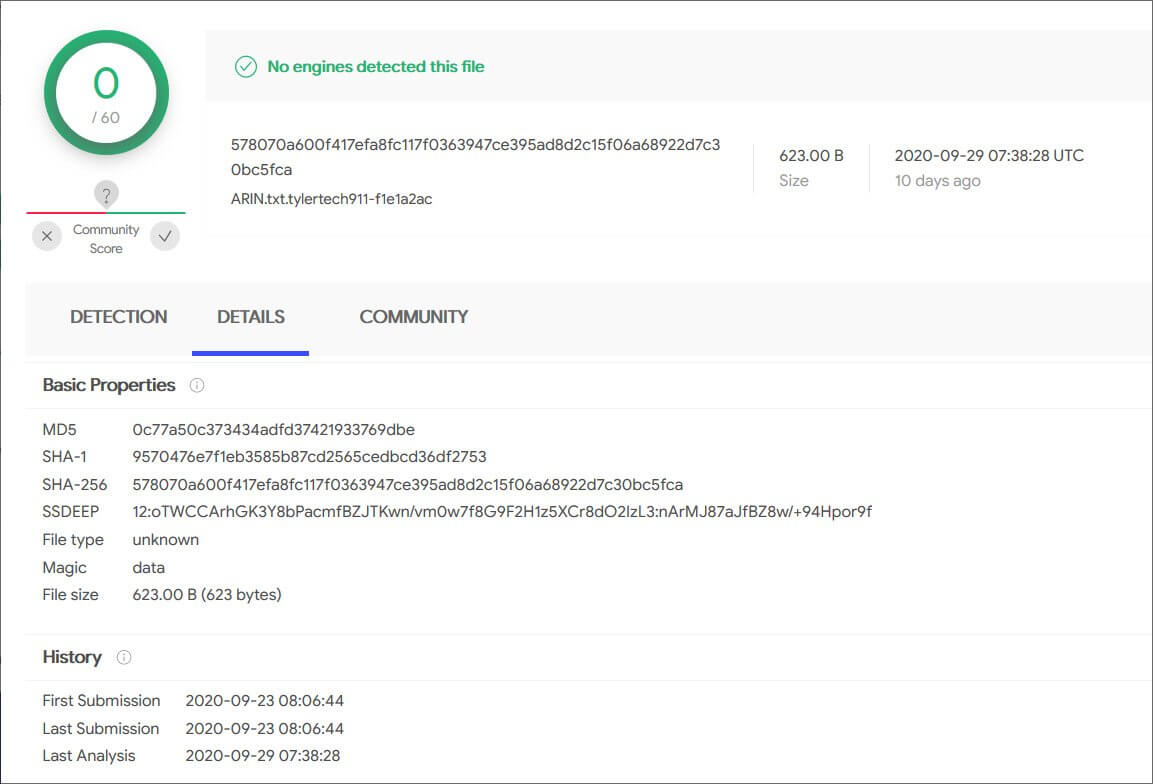
When asked about the decryptor, Tyler Technologies did not deny any ransom payment, declaring that they could not disclose any further information at this time.
Given the sensitivities around the incident and our investigation of it, and our active cooperation with law enforcement, we are not at liberty to disclose additional details at this time.
Since the attack happened no information was leaked online so it might be safe to assume that the attackers kept their word in this case, but we can consider this a happy outcome as paying the ransom does not guarantee that your or your organization’s data will remain safe.
Therefore, it’s safe to say that it’s better to be prepared when it comes to cyberattacks than to find yourself in a compromising situation being forced to pay a ransom.
Ransomware Protection Basics
Businesses of all sizes from all over the world are becoming targets of ransomware attacks.
Layered defenses against this type of threat have proven to be by far the most efficient solution to this continuous threat.
With the work environment constantly changing any company needs to adapt its network defenses, especially in the current situation in which an increasing number of companies have essential personnel working remotely and accessing important parts of the IT infrastructure also remotely it is paramount to understand the new risks this fresh paradigm is bringing.
There are heightened risks to your network being breached; your employees compromising a password, losing a device loaded with critical information, or simply being a victim of a phishing attack. It is that simple.
That is why employee awareness training needs to happen on a regular basis and make sure all employees are vigilant against cyber-attacks.
Email Protection
High-value target e-mail addresses have become precious commodities. Advanced e-mail protection will allow security experts to follow the unusual activity of e-mail accounts – e-mail forwarding rules, for instance. Unusual logins from unusual locations or other odd behavior on known e-mail accounts with known e-mail users. With advanced e-mail protection, the activity can be stopped on its tracks before creating any damage.
Threat Protection Response
Switches, firewalls, endpoints, and wireless access points, and many more – are just but a few components on your network that can be targeted and compromised by potential cybercriminals. All the activity and information exchange between these points is critical to be monitored and assessed. Most of the time attackers will work their way into your network through the first weak point they can find.
After that their protocol states they need to stay as stealthy as possible so they would not be detected by traditional network tools. Given enough time under the radar, the threat actors will most likely find valuable data and valuable network resources.
Data Backup & Recovery
This is the ultimate fail-safe solution for your all-important data and systems. Regular snapshots of data systems can draw the line between a successful backup solution that stores the snapshots in a secure location and disaster. With relevant and consistent backup, if you fall victim to ransomware, you can just reinstate the latest valid snapshot before the attack.
You should be thinking about your company’s cybersecurity strategy from a holistic point of view and therefore apply a “defense in depth strategy”, that must include:
- patch management.
- email security.
- ransomware encryption protection.
All of the above-mentioned are solutions that can help you deal with all these aspects and can be found in the Heimdal® product suite.
Our Heimdal Patch & Asset Management will help you close vulnerabilities by allowing you to update software and operating systems from a unified dashboard and deploying Windows, 3rd party, and custom software to your endpoints anywhere in the world.
You can add an extra protective layer with our lightweight, easy to deploy, and highly responsive, Heimdal Email Security.
The anti-malware and anti-spam filter can be scaled to any number of endpoints within your organization. Its MX record-based analysis vectors keep all malicious emails out of your inbox, automatically removing malware-laced attachments, filtering emails coming from malicious IPs or domains, or those containing malicious URLs.

Heimdal™ Ransomware Encryption Protection
- Blocks any unauthorized encryption attempts;
- Detects ransomware regardless of signature;
- Universal compatibility with any cybersecurity solution;
- Full audit trail with stunning graphics;
Wrapping Up…
When looking at the Tyler Technology Ransomware attack we should understand the need to pay closer attention to the cybersecurity strategy in place as the growing threat that ransomware poses should be fought with at least an equal response from companies in order to ensure proper risk management and cybersecurity preparedness as it’s best to remember that is easier to prevent negligence than it is to defend it.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








