Contents:
A new S1deload Stealer malware campaign infects YouTube and Facebook users as hackers try to use their devices for cryptocurrency mining.
After they get S1deload Stealer on the victim`s device and obtain a connection to the command-and-control server, threat actors instruct it to perform a task.
The Malware Attack Explained
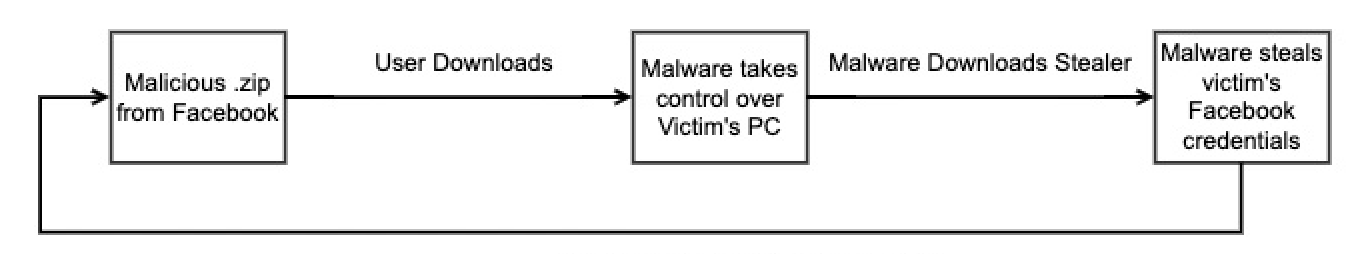
Threat actors use social engineering techniques to trick their victims into installing malware on their devices. Hackers push adult-themed archives in Facebook and YouTube comments and wait for the victims to press download.
When users download an archive they actually get an executable signed with a valid Western Digital digital signature. There is also a malicious DLL (WDSync.dll) that includes the final payload. S1deload Stealer uses DLL sideloading so it can evade detection.
According to researchers:
It can download and run additional components, including a headless Chrome web browser that runs in the background and emulates human behavior to artificially boost view counts on YouTube videos and Facebook posts.
On other systems, it can also deploy a stealer that decrypts and exfiltrates saved credentials and cookies from the victim’s browser and the Login Data SQLite database or a cryptojacker that will mine BEAM cryptocurrency.
The malware steals browser-saved credentials and exfiltrates them to the malware author’s server. The credentials are, of course, used to trick more victims on social media and take control of other machines.
Once it steals a Facebook account, the malware leverages the Facebook Graph API to check how interesting the victim is. Hackers rather go after Facebook pages or group admins, ads payers, or profiles that are linked to a business manager account.
How to Avoid Falling Victim to S1deload Stealer
There are two things you must do to protect your Facebook or Youtube account from S1deload Stealer and malware in general.
- Don`t run executables from unknown sources, under no circumstances.
- Never miss a patch or update for your anti-malware protection.
There are lots of other types of info-stealers lurking on the web and on social media. Stay on guard when you press the download button and use a professional cybersecurity solution to secure endpoints.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and Youtube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







