Contents:
More than 1,600 publicly available images on Docker Hub were found to hide malicious behavior, including DNS hijackers, cryptocurrency miners, website redirectors, and embedded secrets that can be used as backdoors.
Docker images serve as templates for quickly and easily building containers with pre-built code and applications. As a result, those looking to launch new instances frequently use Docker Hub to find an application that can be quickly deployed.
According to BleepingComputer, over a thousand malicious uploads pose serious hazards to unaware users who deploy malware-filled pictures on locally hosted or cloud-based containers as a result of threat actors abusing the service.
Threat actors have published infected photos with names that make them appear to be well-known and reliable projects in order to deceive consumers into downloading them.
What Hides Behinds the Traps?
Besides the images reviewed by the Docker Library Project, which are verified to be trustworthy, thousands of images with an unknown status are available on the platform.
Researchers at Sysdig used their automated scanners to verify 250,000 unverified Linux images, identifying 1,652 of them as being malicious in the process.
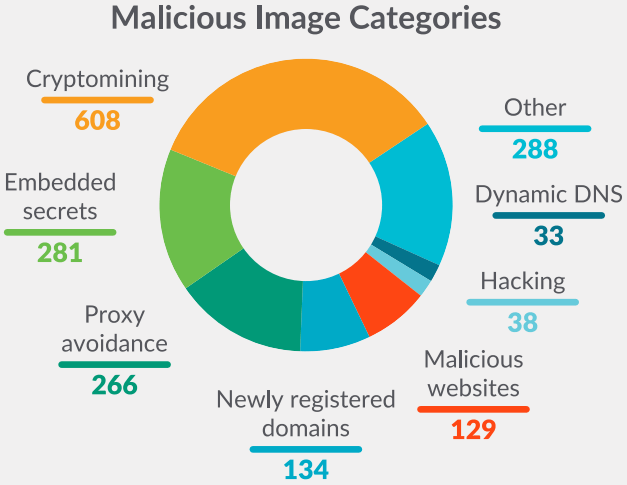
Types of malware found in the images on Docker Hub (Source: Sysdig)
The most prevalent category was crypto-miners, with 608 container images, followed by embedded secrets measuring 281 confirmed cases. The embedded secrets detected in the images are AWS credentials, SSH keys, GitHub tokens, NPM tokens, and others.
According to Sysdig, these secrets may have been inadvertently inserted by the threat actor who developed and uploaded the public photos or purposely left them.
Many of the identified malicious images used typosquatting to impersonate legitimate and trusted images. Some cases had a high rate of success, with two examples being downloaded almost 17,000 times.
An Increasing Problem
The risk to users is increasing as 61% of all images pulled from Docker Hub in 2022 come from public repositories, up 15% from 2021 statistics. Unfortunately, due to the size of the Docker Hub public library, its administrators are unable to review every upload on a daily basis; as a result, many malicious images go unreported.
Researchers also noticed that most threat actors upload a small number of malicious images, so even if the uploader is banned, the threat landscape of the platform remains almost the same.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








