Contents:
Recently, Cofense Phishing Defense Center analysts discovered a rather unusual PayPal credential phishing scam.
Phishing is a malicious technique used by cybercriminals to gather sensitive information (credit card data, usernames, and passwords, etc.) from users. The attackers pretend to be a trustworthy entity to bait the victims into trusting them and revealing their confidential data. What’s worse, the data gathered through phishing can be used for financial theft, identity theft, to gain unauthorized access to the victim’s accounts or to accounts they have access to, to blackmail the victim, and more.
PayPal Credential Phishing Technique
Since credential phishing is usually conducted via a simple URL link, it is easy to overlook some subtle or exaggerated tactics that threat actors have been using to steal credentials from unsuspecting victims.
As we can see from the email below, this particular attack does not look entirely sophisticated or even seriously suspicious.
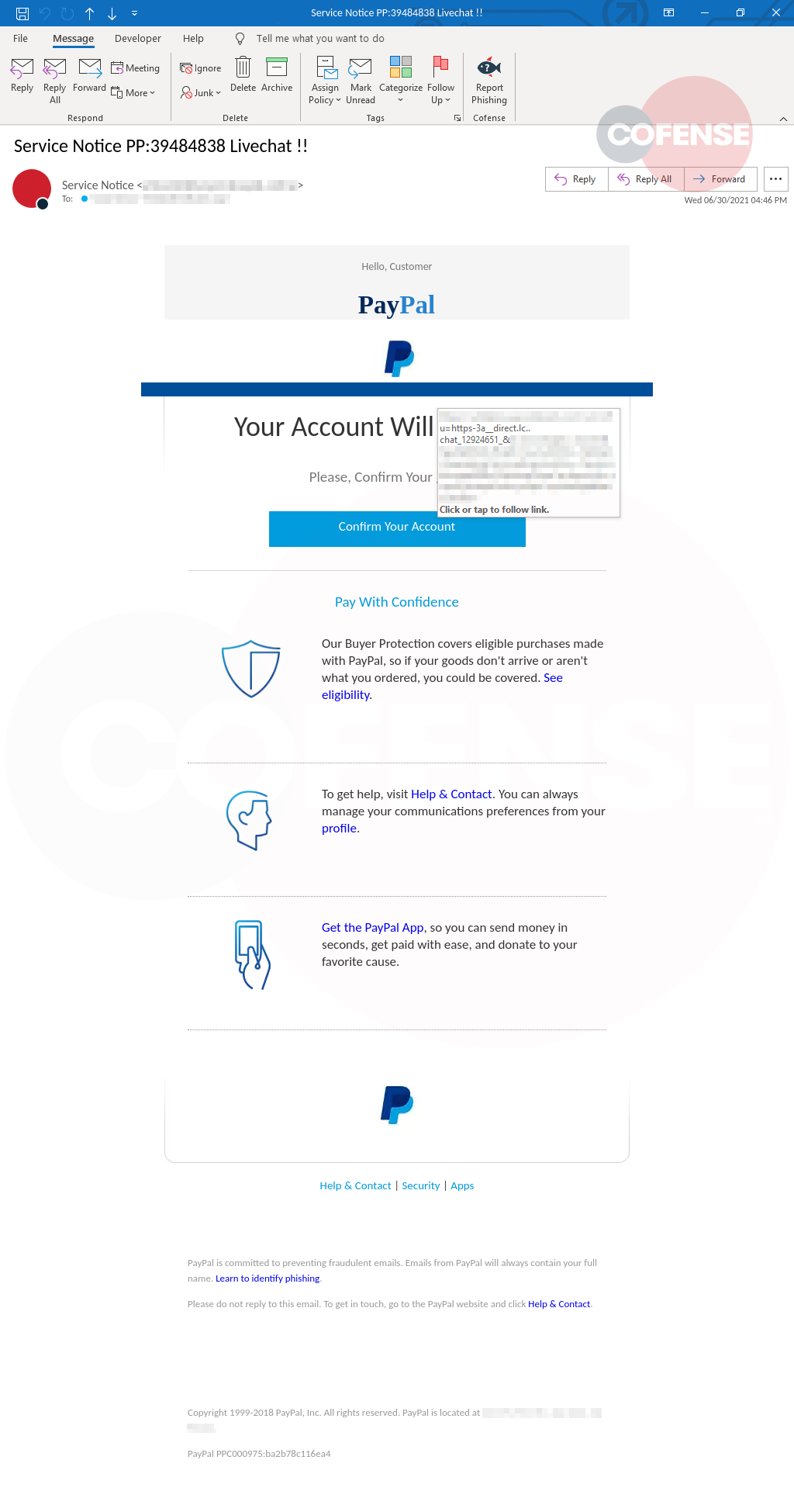
Image Source: Cofense Phishing Defense Center
Threat analyst Alex Geoghagan explains that although this email may rush the target into attempting to have the problem resolved quickly, the attacker made no attempts at masking the “from” address, which was identified as one that’s not associated with an actual PayPal email.
However, the email body is well put together and contains links that anyone would expect to find in a legitimate email from any service.
There is a “Help & Contact” link, as well as an (ironic) “Learn to identify Phishing” link in the body of the email, both leading to authentic PayPal links. Beyond the first clue in the sender email address, when hovering over the button labeled “Confirm Your Account,” it does not lead to a PayPal URL. It instead leads to a URL at direct[.]lc[.]chat. A user familiar with PayPal may notice at this point that they are being taken to a domain outside of PayPal, while the legitimate PayPal live chat is hosted within the PayPal domain and requires that you log in to use it.
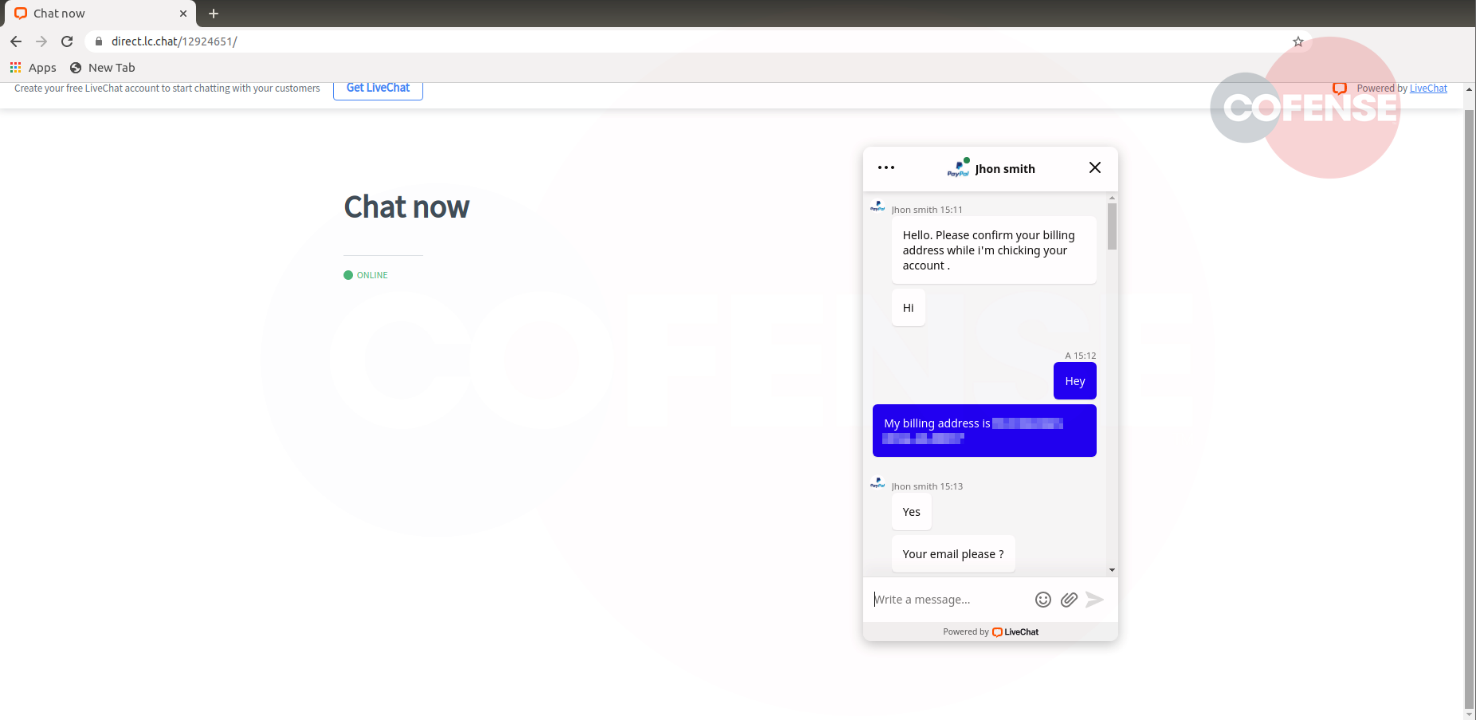
Image Source: Cofense Phishing Defense Center
How Does It Work?
Once the fraudulent live chat is accessed, the attacker uses automated scripts to initiate communication with the victims and try to get their addresses, email addresses, and phone numbers. In short, the threat actor is collecting this information to convey legitimacy and gather enough data for authentication.
After acquiring all this information, the hacker will try to get the victims’ PayPal credentials. Finally, using the phone number provided earlier, a verification code is sent via SMS to the target to make sure this is the individual who has access to the device.
This attack demonstrates the complexity of phishing attacks that go beyond the typical “Forms” page or spoofed login. In this case, a carefully crafted email appears to be legitimate until a recipient dives into the headers and links, which is something your average user will most likely not do.
Recognizing attacks that target your communications is the foundation of a successful phishing prevention strategy. When coupled with a strong suite of cybersecurity solutions, this knowledge is what can protect your private data in the long run. For this reason, investing in continuous awareness training is the first thing to do.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








