Contents:
Memento ransomware group makes its way on the threat landscape scene. Their approach seems to be quite uncommon, as the threat actor group locks files in WinRAR archives protected by a password. Because security software managed to detect previous encryption techniques, they have chosen now this method instead.
Memento Ransomware Group: Background
Sophos researchers published a report on this topic. It seems that the Memento ransomware group has started its ransomware activity in October 2021. They targeted a vulnerability in the VMware vCenter Server web client in order to obtain initial access to the targeted networks. The flaw was dubbed CVE-2021-21971, being characterized by a 9.8 severity score and representing basically a remote code execution vulnerability.
Anyone that remotely accesses a vCenter server’s TCP/IP port 443 can manage through the abusing of this vulnerability to use privileged access in order to perform commands execution on the operation system. It seems that the vulnerability received a patch back in February, however, not many enterprises seemed to apply this patch.
Apparently, Memento started exploiting this flaw in April, and then last month they went on with their ransomware operation. They targeted vCenter and started performing a series of actions like server admin credentials extraction, scheduled tasks enforcing for persistence purposes and further moving laterally across the network by means of RDP over SSH.
How Did the Encryption Phase Unfold?
As BleepingComputer mentions, when the reconnaissance phase was over, they put the stoled data in a WinRAR archive and then exfiltrated it.
They removed their traces by means of Jetico’s BCWipe which is basically a utility that helps with data wiping. Then, next, the AES encryption was employed through a Python-based ransomware strain.
The Memento attack flow is illustrated below.
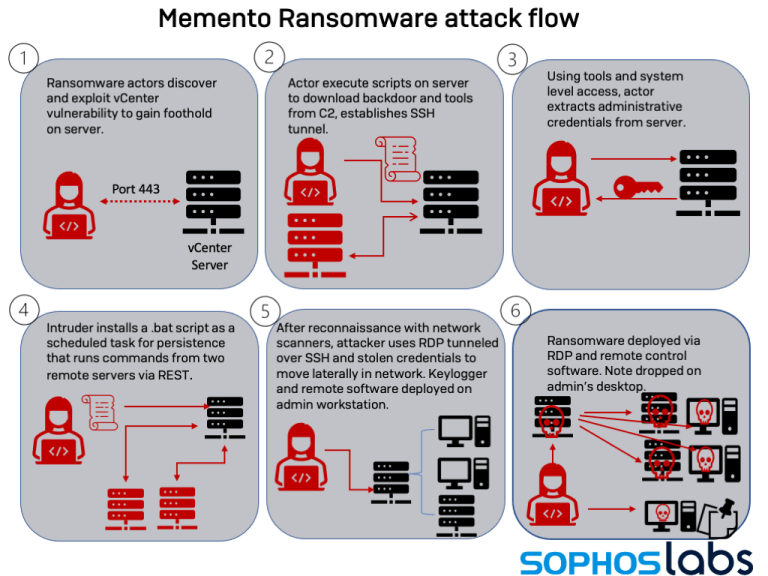
What Led to the Unusual Workaround?
The same report shares details on how the Mememto ransomware group came to the use of encrypted files inside the archive.
It seems that their original encryption attempts were detected by security protection, so to avoid encryption, they chose a different method and thus used password-protected archives to move the file in there. The process unfolds like this: files are moved into WinRAR archives, then a strong password is set up, that key is encrypted and the original files deleted.
Victims came across a ransom demand of 15.95 BTC ($940,000) for the total restoration or they have to pay 0.099 BTC ($5,850) for every file.
Researchers have underlined that:
Instead of encrypting files, the “crypt” code now put the files in unencrypted form into archive files, using the copy of WinRAR, saving each file in its own archive with a .vaultz file extension. (…) Passwords were generated for each file as it was archived. Then the passwords themselves were encrypted.
How to Stay Safe Using Heimdal™?
Ransomware is a very popular threat nowadays. To keep it away, you need a good Ransomware Encryption Protection tool like ours. A 100% signature-free solution, it keeps you protected from data loss and data exfiltration, being compatible with any antivirus. What’s also cool is that you can view details of a malicious encryption incident report from the Heimdal™ Dashboard.
Did you enjoy this article? Follow us on LinkedIn, Twitter, Facebook, Youtube, or Instagram to keep up to date with everything we post!










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








