Contents:
Backstage, the open-source developer portal from Spotify, has been discovered as vulnerable to a high-severity security flaw that could grant threat actors the possibility to execute remote code by leveraging a recently disclosed bug in a third-party module.
The vulnerability has a CVSS score of 9.8 and takes advantage of a critical sandbox escape in vm2, the popular JavaScript sandbox library, tracked as CVE-2022-36067, CVSS score 10 and codenamed Sandbreak.
An unauthenticated threat actor can execute arbitrary system commands on a Backstage application by exploiting a vm2 sandbox escape in the Scaffolder core plugin.
Diving Deeper
Backstage is the first open-source infrastructure platform by Spotify, and it allows its users to create, manage, and explore software components from a unified perspective. It’s used by companies such as Netflix, DoorDash, Roku, Expedia, American Airlines, Fidelity Investments and Epic Games.
According to Oxeye`s report, the flaw begins from a tool called “software templates” which is normally used to create components within Backstage. Although the template engine utilizes vm2 to mitigate the risk associated with running untrusted code, the existence of the Sandbreak flaw makes it possible to execute arbitrary system commands outside of the security perimeter.
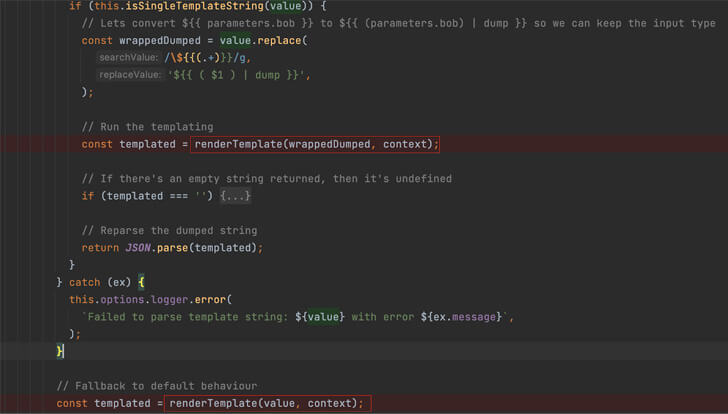
Oxeye further claimed more than 500 exposed Backstage instances were identified, all of which could potentially be weaponized by attackers without requiring any authorization.
In their takeaways on the matter, the Israeli cybersecurity company noted that: “The root of any template-based VM escape is gaining JavaScript execution rights within the template. By using ‘logic-less’ template engines such as Mustache, you can avoid introducing server-side template injection vulnerabilities.”
As The Hacker News reports, the issue was addressed in a new version released on August 29, 2022, following the initial disclosure on the 18th of the same month.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







