Contents:
The BlackByte ransomware has returned with an advanced version of its operation, including a new data leak website using novel extortion strategies that were taken from LockBit.
More About the BlackByte Ransomware Gang
The BlackByte ransomware started targeting corporate networks throughout the globe in July 2021, when it first appeared on the scene.
Their most well-known strike was against the NFL’s 49ers, but according to a joint FBI and Secret Service advisory, they were also behind attacks on important infrastructure sectors like government entities, financial institutions, and food & agriculture.
Just like its other ransomware fellows, BlackByte targets its victim’s files by applying encryption to them. Afterward, the BlackByte ransomware victims usually receive a ransom note on their computer screen, which says that they have to pay a ransom in order to have their files decrypted.
Following a short hiatus, the ransomware campaign is currently pushing a brand-new data leak website on hacker forums and via Twitter accounts that are under the gang’s control.
While it is unclear if the ransomware encryptor has also changed, the ransomware group has created a new Tor data leak site. They are dubbing this latest version of their operation BlackByte version 2.0.
The data leak site currently has only one victim, but it now employs new extortion techniques that let victims pay to download their data ($200,000), extend the period it is published ($5,000), or completely erase all the data ($300,000). Depending on the size/income of the victim, these costs may vary.
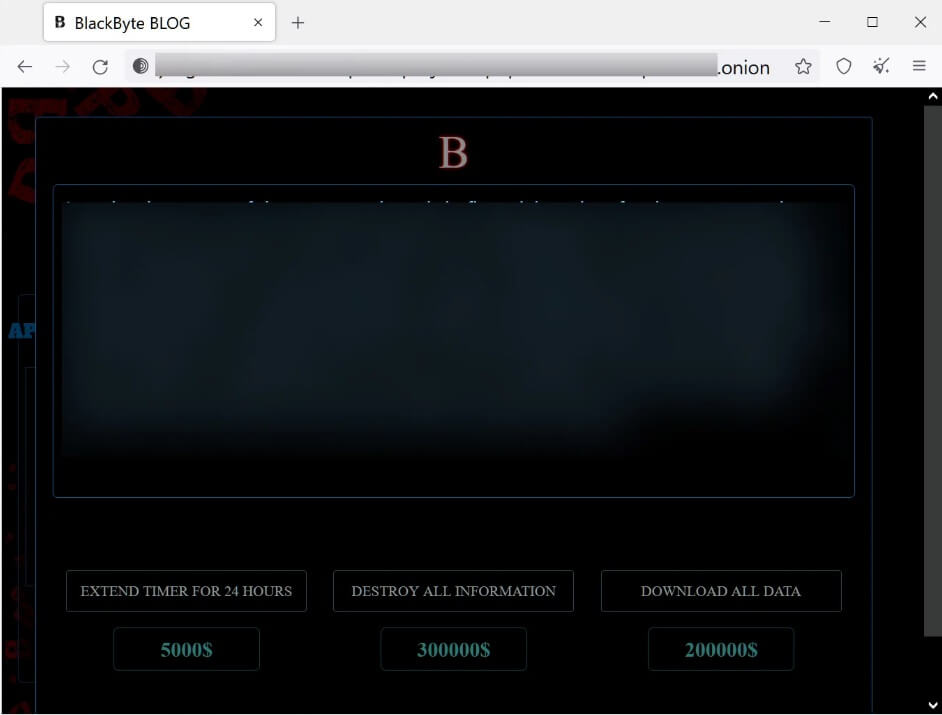
According to cybersecurity intelligence company KELA, the new functionalities of BlackByte’s data leak site are now faulty because the Bitcoin and Monero addresses that “clients” can use to buy or delete the data are not correctly embedded.
The first rule of a ransomware gang is: if you aim to receive ransom, provide your wallet. Doesn’t look like new #BlackByte is going to receive any payments… pic.twitter.com/YJpDyHUa5M
— KELA (@Intel_by_KELA) August 17, 2022
These new extortion methods intend to let the victim pay to have their data removed while leaving it available for other cybercriminals to buy if they want to.
With the release of its 3.0 version, LockBit incorporated the same extortion techniques, which are viewed more as a novelty than as effective extortion methods.
How Can Heimdal™ Help?
In the fight against ransomware, Heimdal™ Security is offering its customers an outstanding integrated cybersecurity suite including the Ransomware Encryption Protection module, that is universally compatible with any antivirus solution, and is 100% signature-free, ensuring superior detection and remediation of any ransomware, whether fileless or file-based (including the most recent ones like LockFile).
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








