Contents:
A new critical-severity vulnerability in TeamCity On-Premises is being exploited by threat actors. CVE-2024-27198 is an authentication bypass vulnerability with a critical severity score of 9.8 out of 10.
It affects all versions through 2023.11.4 of TeamCity’s on-premises edition software.
The exploitation appears to be massive. Hundreds of new users created on unpatched instances of TeamCity are being exposed on the public web.
Over 1,700 Vulnerable Servers
According to BleepingComputer, a little over 1,700 TeamCity servers are vulnerable and at risk of being used in supply-chain attacks.
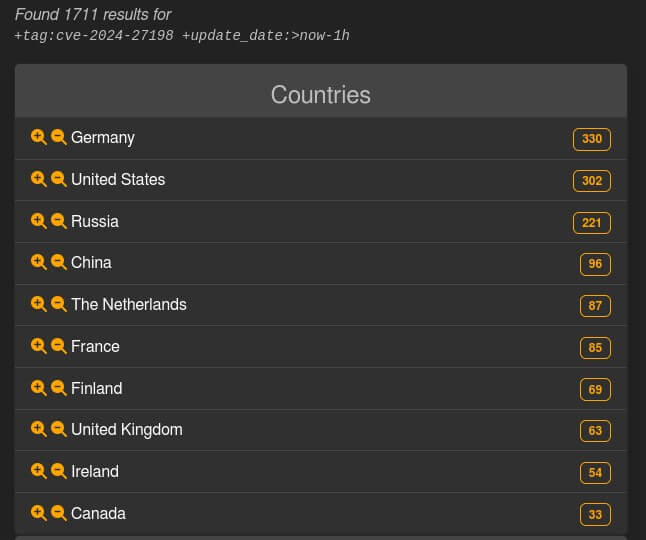
TeamCity Installations Vulnerable to CVE-2024-27198 (Source)
Most of the vulnerable hosts indexed by LeakIX, a search engine used for exposed device misconfigurations and vulnerabilities, appear to be located in Germany, the United States, and Russia. The site shows that over 1,440 of these have already been compromised by hackers.
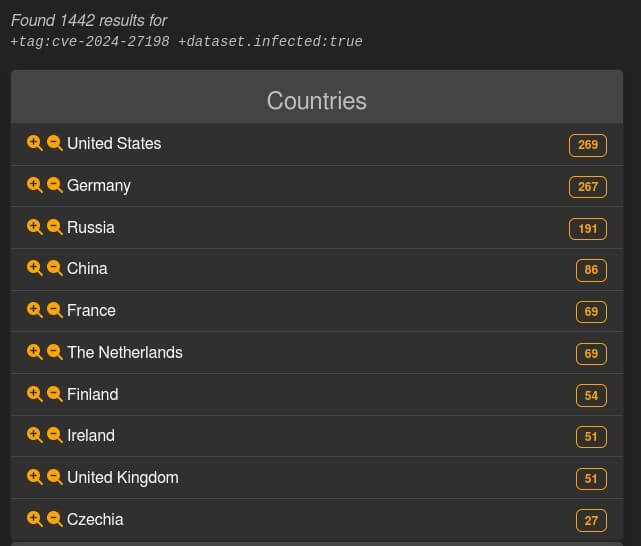
Instances Compromised Through CVE-2024-27198 (Source)
Cybersecurity researchers recorded a sharp increase in attempts to exploit the vulnerability, most of them coming from systems in the United States on the DigitalOcean hosting infrastructure.
Gregory Boddin of LeakIX noted that the TeamCity servers observed are production machines used to build and deploy software.
Because they might contain private information like login credentials for the environments (e.g., stores and marketplaces, repositories, firm infrastructure) where code is published, distributed, or kept, breaching them could result in supply-chain assaults.
TeamCity Update
The vulnerability can be found in the server’s web component and gives an unauthenticated remote attacker the ability to take over a vulnerable server and provide them administrator access.
JetBrains was informed about the vulnerability in mid-February and on March 4 they fixed it. TeamCity 2023.11.4, which includes a fix for CVE-2024-27198, was announced by JetBrains on Monday. The company encourages all customers to update their instances to the most recent version.
Administrators of on-premise TeamCity instances should install the most recent release immediately, as widespread exploitation has already been reported.
If you liked this piece, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








