Contents:
European government personnel involved in helping Ukraine refugees with logistics support has been the target of a spear-phishing campaign, a new report underlines.
Spear-Phishing Campaign Against Countries Helping Ukraine Refugees
A recent analysis belonging to Proofpoint researchers unveils a spear-phishing campaign where threat actors make use of email accounts that are “possibly compromised” belonging to Ukrainian armed service members to spread phishing messages.
Proofpoint has identified a likely nation-state sponsored phishing campaign using a possibly compromised Ukrainian armed service member’s email account to target European government personnel involved in managing the logistics of refugees fleeing Ukraine. The email included a malicious macro attachment which attempted to download a Lua-based malware dubbed SunSeed.
According to the researchers, only European governmental entities have been targeted in this malicious campaign for the moment and they were not able currently to link the cyberattacks to any threat actor.
The targeted individuals possessed a range of expertise and professional responsibilities. However, there was a clear preference for targeting individuals with responsibilities related to transportation, financial and budget allocation, administration, and population movement within Europe. This campaign may represent an attempt to gain intelligence regarding the logistics surrounding the movement of funds, supplies, and people within NATO member countries.
However, as the experts further underline, looking at the infection chain, this campaign is most probably tied to some phishing attacks that happened in July last year that were correlated to Ghostwriter, also known TA445 or UNC1151. The current spear-phishing campaign under discussion was tracked as Asylum Ambuscade.
Here is a snapshot of the campaign revealed in the report:
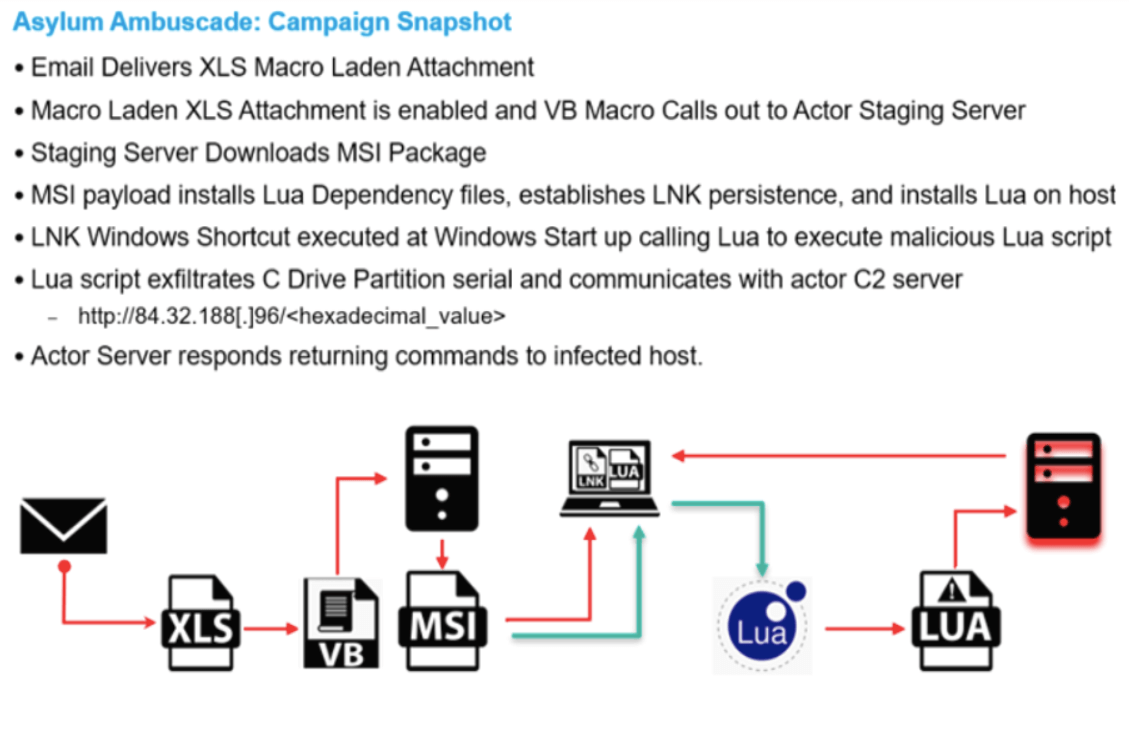
In November 2021, researchers from Mandiant linked Ghostwriter threat actor group to the Belarusian government. Since the beginning of the recent conflict in Ukraine, Ghostwriter was correlated to other cyberattacks targeting Ukraine. In this sense, according to the BleepingComputer publication, CERT-UA (the Computer Emergency Response Team of Ukraine) warned on the attempts of Ghostwriter to hack Ukrainian military officers’ private email accounts in order to distribute phishing emails to their contacts‘ list.
Accounts employed by Ghostwriter to target Ukrainian authorities and military personnel on Facebook platforms were also removed by the company on Monday. Furthermore, Facebook mentioned that they managed to block some phishing domains leveraged to get into Ukrainian consumers’ accounts.
How Does Asylum Ambuscade Resemble Ghostwriter in Techniques?
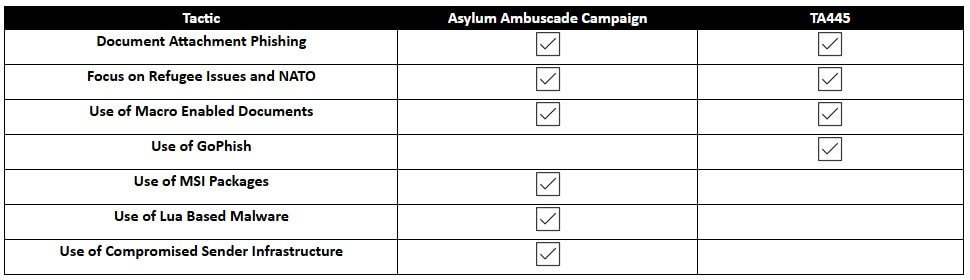
Proofpoint researchers also provided in their report a comparison between the methods employed by Asylum Ambuscade, the current spear-phishing campaign and Ghostwriter.
If you liked this article, follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








