Contents:
Cybersecurity researchers recently discovered a new wave of ChromeLoader malware that threat actors are using to circumvent antivirus software and other cybersecurity measures.
As part of the ChromeLoader malware campaign, cybercriminals now use VHD files instead of the typical ISO optical disc image format. According to the Security Emergency Response Center (ASEC) experts at AhnLab Security, in order to gain access to sensitive information or to take control of users’ systems, attackers use deceptive file names to lure them into downloading and running malware.
What Are the Malicious Filenames?
Below is a list as compiled by CSN, of all the filenames that are being actively exploited:
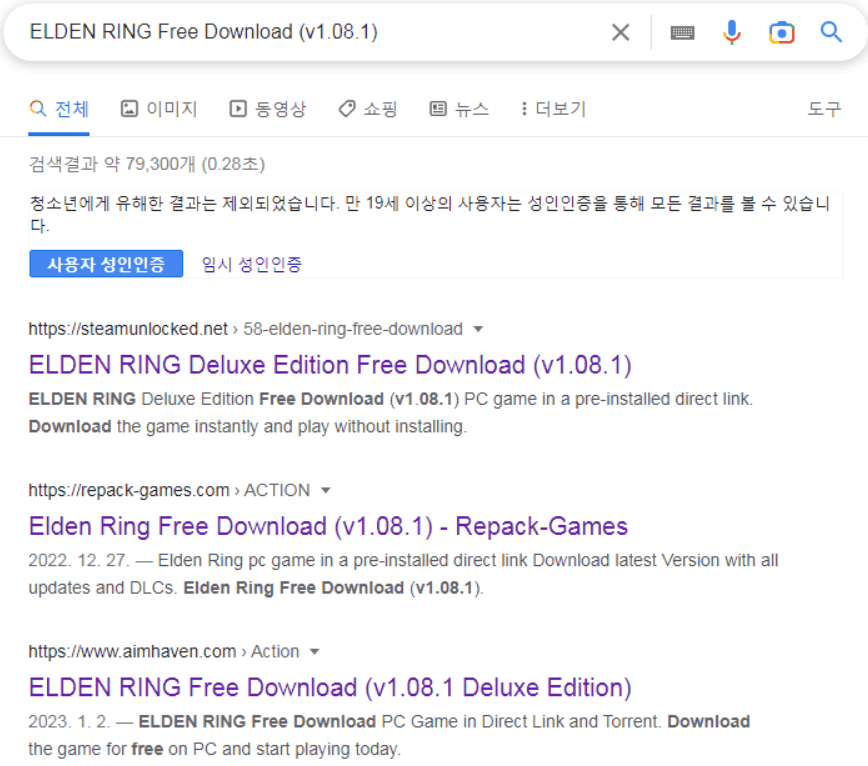
- ELDEN RING Free Download (v1_08_1).vhd
- Dark Souls 3 [FitGirl Repack]_part1_rar.vhd
- Red Dead Redemption 2 Free Download (v1_0_1436_28).vhd
- File_ Need for Speed Carbon Collectors Edition____.vhd
- File_ Call of Duty Deluxe Edition_zip ___.vhd
- File_ Portal_2_v2023_01_17_zip ___.vhd
- File_ Minecraft – Story Mode_Complete Season_zi___.vhd
- [NEW] ROBLOX _ Doors Script _ Hack _ Spawn Enti___.vhd
- The Legend of Zelda_ Breath of the Wild SWITCH ___.vhd
- Pokemon Ultra Moon_ Update 1_2 [Decrypted] 3DS ___ (1).vhd
- Animal-Crossing-New-Horizons-Switch-NSPNSZXCI-U___.vhd
- Mario Kart 8 Deluxe (NSP)(Booster Course DLC)(W___ (2).vhd
- Super Mario Odyssey Switch NSP+ Update Free Dow___.vhd
- Microsoft Office 2010 Free Download.vhd
- Adobe Photoshop 2023 Free Download.vhd
In addition to the Install.lnk file, all other files associated with the ChromeLoader malware campaign have the “hidden” property enabled, meaning that when viewed by ordinary users, only the Install.lnk file is visible.
Recently, there has been an increase in malware using disk image files. Disguising malware as game hacks and crack programs is a method employed by many threat actors. Users must be particularly cautious about executing files downloaded from unknown sources, and it is advised that users download programs from their official websites.
How Does It Work?
Initially appearing as a credential-stealing browser hijacker, the ChromeLoader malware first surfaced in January 2022. Since then, it has been constantly evolving, becoming more and more sophisticated. The malware is designed to generate revenue from ad clicks and other unethical activities, but its impact can go beyond simple advertising fraud. Its ability to compromise popular browsers, such as Google Chrome, is at the heart of ChromeLoader’s functionality. Once the malware has gained access to a user’s browser, it can change various browser settings, redirecting internet traffic to potentially harmful websites.
Its other capabilities amount to:
- Steal sensitive data.
- Deploy ransomware.
- Drop decompression bombs.
Safe browsing habits and avoiding clicking on suspicious links are essential for minimizing the risk of falling victim to malware threats like ChromeLoader. Avoid downloading files from unknown or untrusted sources!
If you liked this article, follow us on LinkedIn, Twitter, Facebook, and YouTube for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security







