Contents:
Recently, Binance has been taking part in an international investigation with US Law Enforcement, Ukraine Cyber Police, Cyber Bureau of Korean National Police Agency, Spanish Civil Guard, and Swiss Federal Office of Police, among others, to capture a prolific cybercriminal ring.
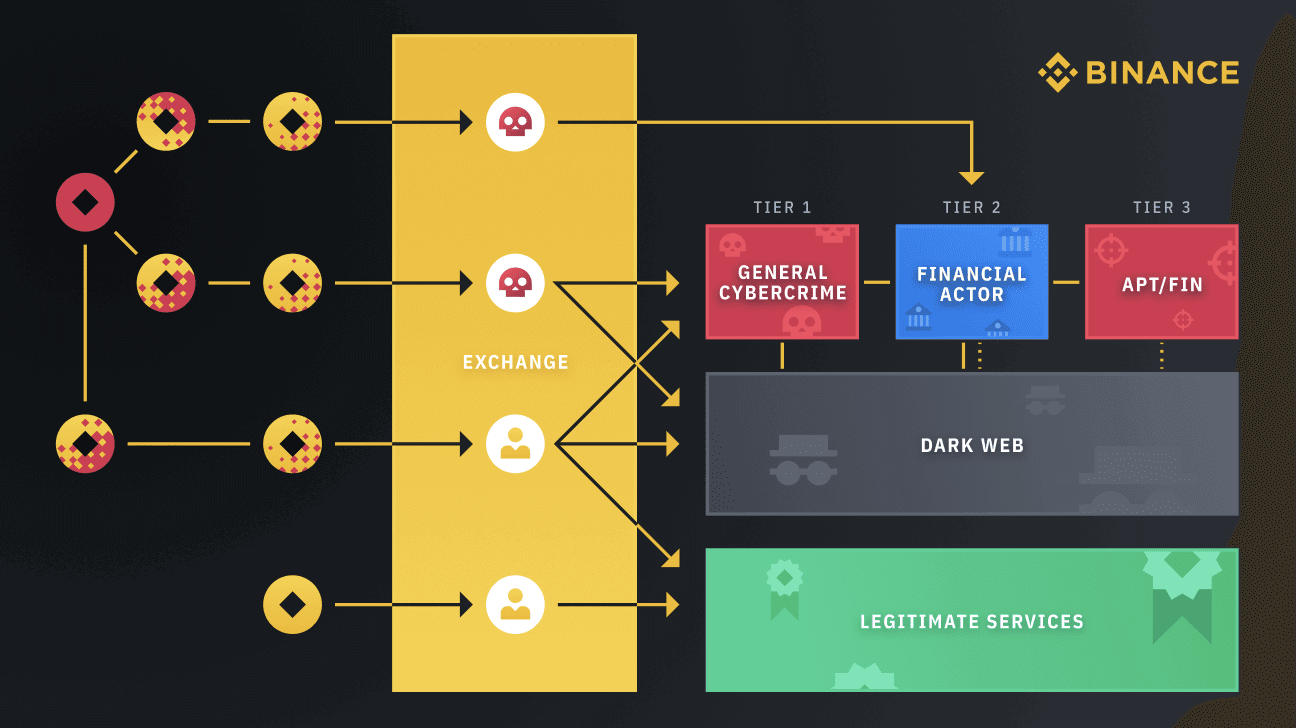
Image Source: Binance
According to the blockchain company, the threat actors – referred to as FANCYCAT – were laundering money obtained from ransomware attacks and other illegal activities.
Binance also informed that its security division played a major role in the international investigation that led to the arrest of multiple members of the Clop ransomware gang.
Clop Ransomware is a dangerous file-encrypting virus that actively avoids the security unprotected system and encrypts the saved files by planting the .Clop extension. It exploits AES cipher to encrypt pictures, videos, music, databases papers, and attach .CLOP or .CIOP file extension, which prevents victims from accessing personal data. For example, “sample.jpg” is renamed to “sample.jpg.Clop”.
This way, the victims are pressured into paying the ransom within some time limit for the presumed fixing of their data.
The group — also known as FANCYCAT — has been running multiple criminal activities: distributing cyber attacks; operating a high-risk exchanger; and laundering money from dark web operations and high-profile cyber attacks such as Cl0p and Petya ransomware. In all, FANCYCAT is responsible for over $500M worth of damages in connection with ransomware and millions more from other cybercrimes.
Since more and more threat actors are taking advantage of legitimate cryptocurrency exchanges for money laundering purposes, Binance has been improving its techniques of detecting and analyzing cybercriminals’ cashout activity.
Based on our research and analysis, as well as our understanding of cybercriminals’ history and cashout tactics, we arrived at the conclusion that the biggest security problem in the industry today is money connected to cyber attacks being laundered through nested services and parasite exchanger accounts that live inside macro VASPs, including exchanges like Binance.com. These criminals enjoy taking advantage of reputable exchanges’ liquidity, diverse digital asset offerings and well-developed APIs.
Binance has determined suspicious activity on its service and created a cluster of suspects by employing its AML detection and analytics program.
The company worked with two private-sector chain analytics companies (TRM Labs and Crystal) to analyze on-chain activity and gain a better understanding of this group and its attribution. As resulted from their investigation, this specific group was not only associated with laundering Cl0p attack funds, but also with Petya and other illegally sourced funds. This ultimately led to the identification and eventual arrest of FANCYCAT.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








