Contents:
VMware ESXi is a hypervisor created by VMware that is of the enterprise-class and type-1 varieties. It is used for installing and servicing virtual machines.
ESXi is a type-1 hypervisor, which means that it is not a software program that is put on an operating system; rather, it incorporates and integrates essential OS components, such as a kernel, inside itself. This makes it unique from other types of hypervisors.
The virtualization platform is widely employed by huge enterprises all over the globe; hence, encrypting these platforms often results in a significant interruption to the operations of a company.
What Happened?
Cheers is the name of a new piece of ransomware that has been discovered in the cybercrime world. This ransomware has begun its activities by focusing on unprotected VMware ESXi systems.
Researchers working for Trend Micro have identified a new strain of the Cheers ransomware, which they refer to as “Cheerscrypt.”
We recently observed multiple Linux-based ransomware detections that malicious actors launched to target VMware ESXi servers, a bare-metal hypervisor for creating and running several virtual machines (VMs) that share the same hard drive storage. We encountered Cheerscrypt, a new ransomware family, that has been targeting a customer’s ESXi server used to manage VMware files.
In the past, ESXi servers were also attacked by other known ransomware families such as LockBit, Hive, and RansomEXX as an efficient way to infect many computers with ransomware.
Once a VMware ESXi server has been compromised, the threat actors will launch the encryptor. This will cause the encryptor to automatically enumerate the running virtual machines and shut them down.
During the process of encrypting files, the ransomware looks especially for files with the following extensions:.log,.vmdk,.vmem,.vswp, and.vmsn., as ESXi snapshots, log files, swap files, paging files, and virtual disks are all connected with these file extensions.
The “.Cheers” extension will be added to the end of the filename of each and every encrypted file, but the process of renaming files occurs before encryption does. This means that if access permission to rename a file is refused, the encryption will fail, but the file will still be changed even if the access permission is denied.
In order to generate a secret key for the SOSEMANUK stream cipher, the encryption method makes use of a pair of public and private keys. This key is then embedded in each encrypted file. To prevent the private key from being recovered and used again, it is erased once it has been used to produce the secret key.
While the ransomware is searching directories for data to encrypt, it will write ransom notes in each folder. These ransom notes will be called “How To Restore Your Files.txt.”
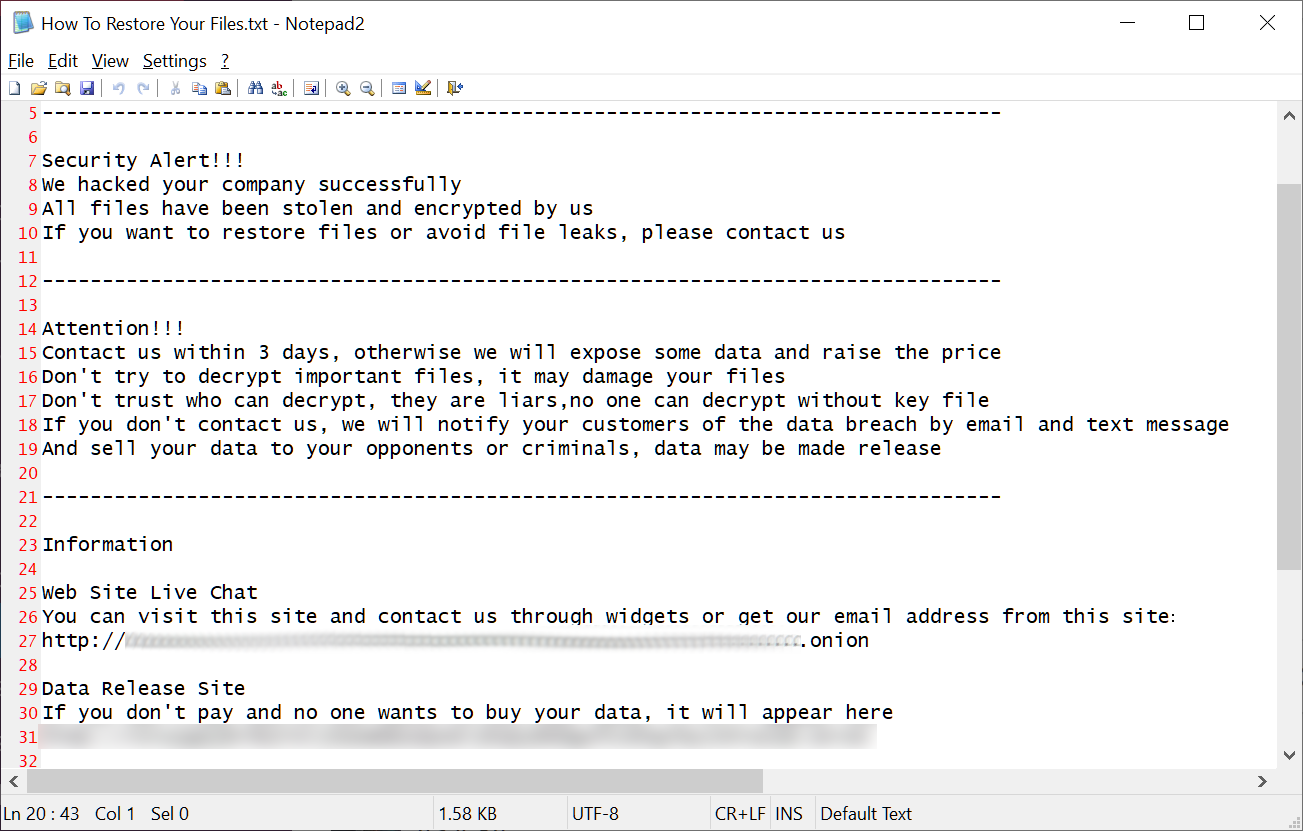
As BleepingComputer explained, these ransom notes provide details on what happened to the victim’s files as well as links to the Tor data leak sites and ransom negotiation sites used by the ransomware campaign.
ESXi is widely used in enterprise settings for server virtualization. It is therefore a popular target for ransomware attacks. As mentioned, compromising ESXi servers has been a scheme used by some notorious cybercriminal groups because it is a means to swiftly spread ransomware to many devices. Organizations should thus expect malicious actors to upgrade their malware arsenal and breach as many systems and platforms as they can for monetary gain.
Make sure you follow us on LinkedIn, Twitter, Facebook, Youtube, and Instagram for more cybersecurity news and topics.










 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management  Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security








