-
Products
-
Solutions
-
Partners
-
Resources
-
Company
- Support
- Call Us : +1 813-670-6169
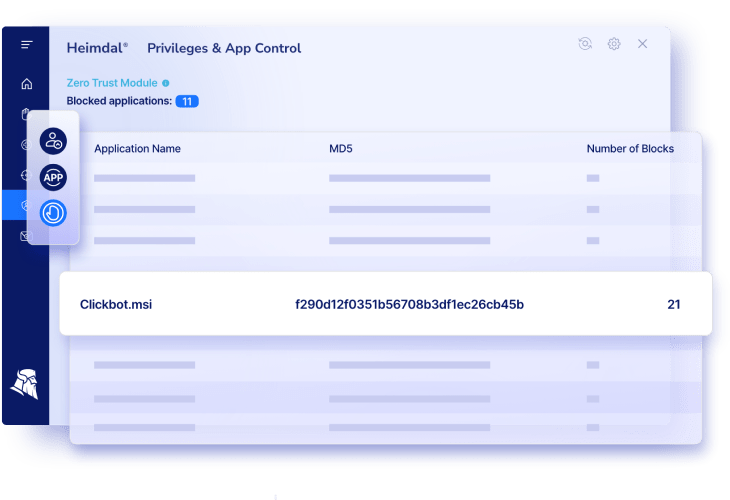
 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
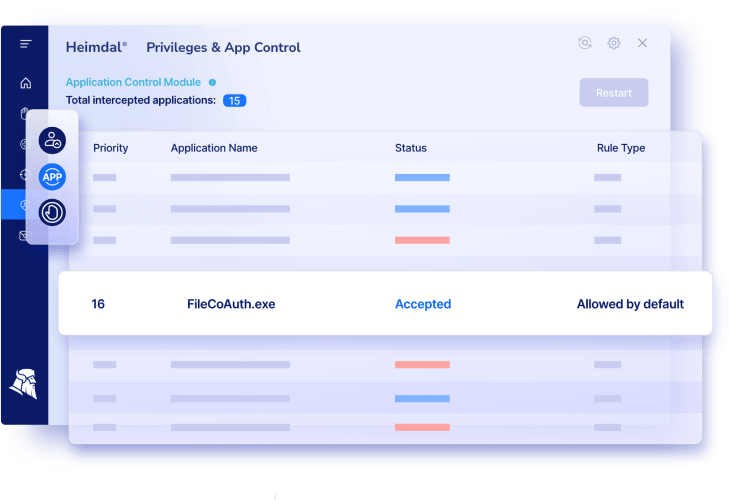
 Endpoint Security
Endpoint Security
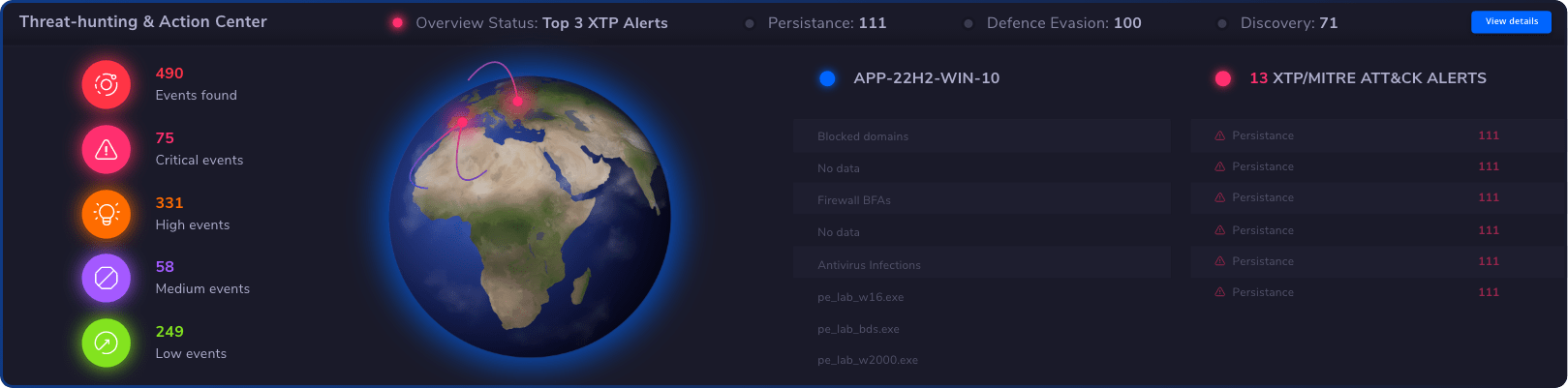
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
PLATFORMS

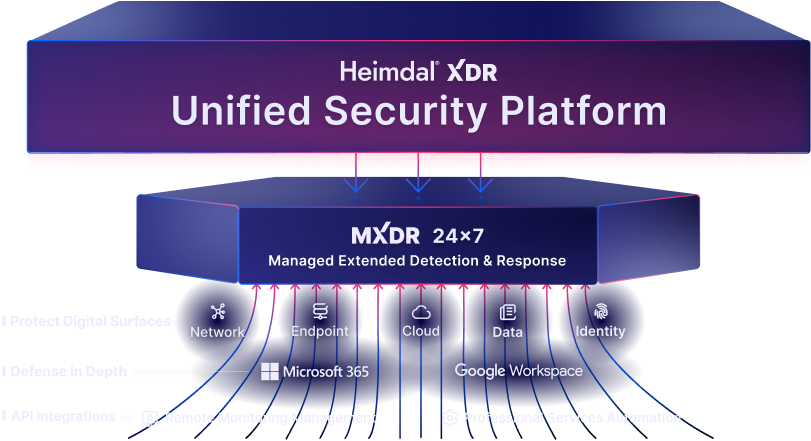
Extended Detection and Response (XDR)
Powered
by Heimdal Unified Security Platform
MANAGED SERVICES

Managed Extended Detection and Response (MXDR)
24x7 SOC Services
INDUSTRIES



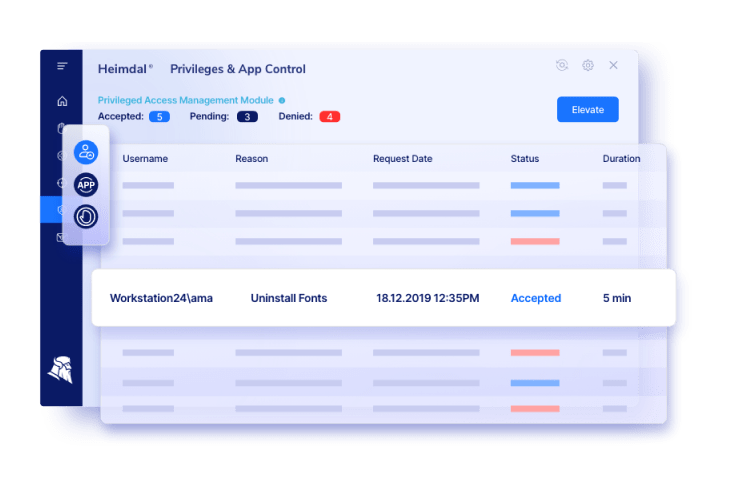
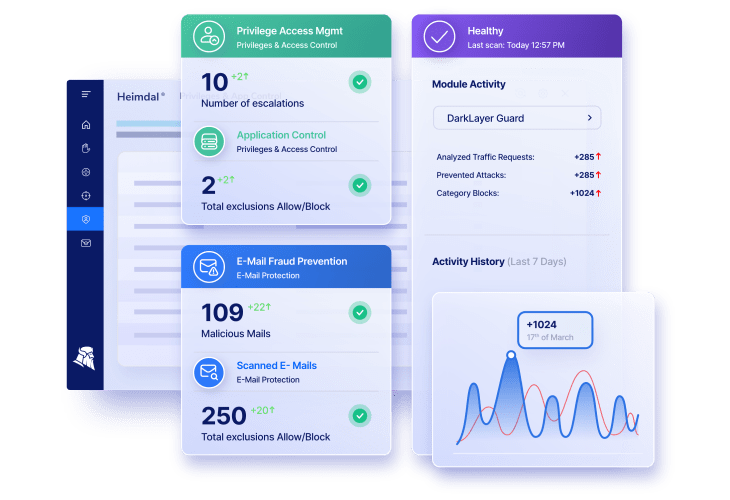
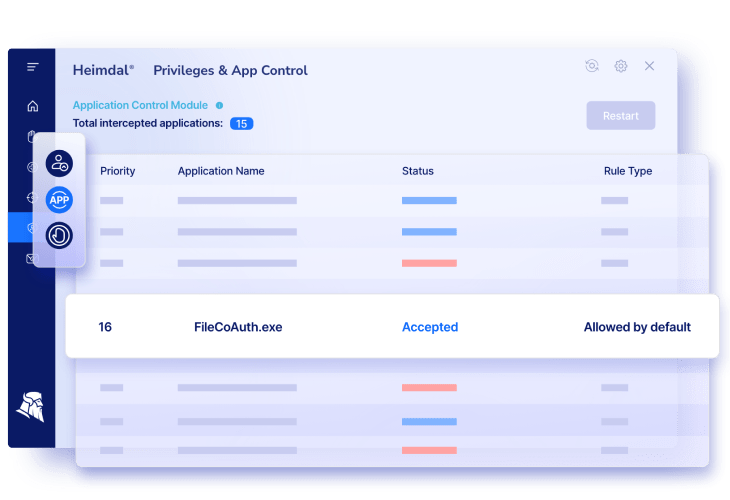
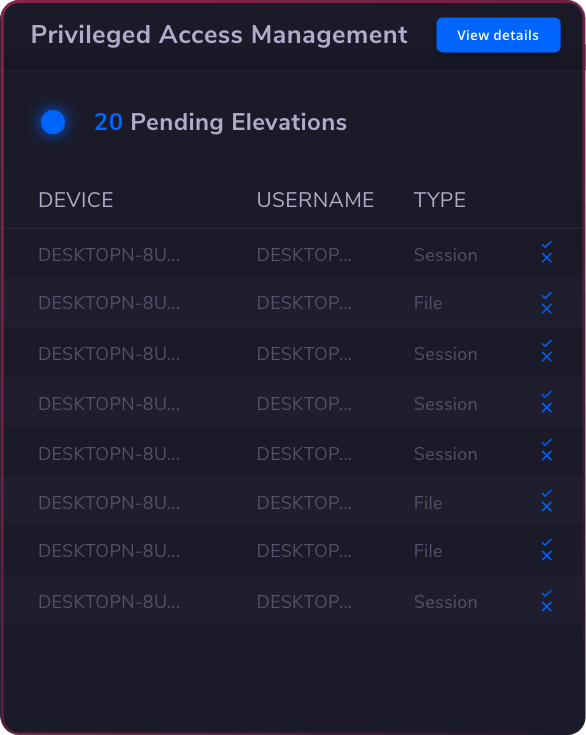
 Privileged Access Management
Privileged Access Management
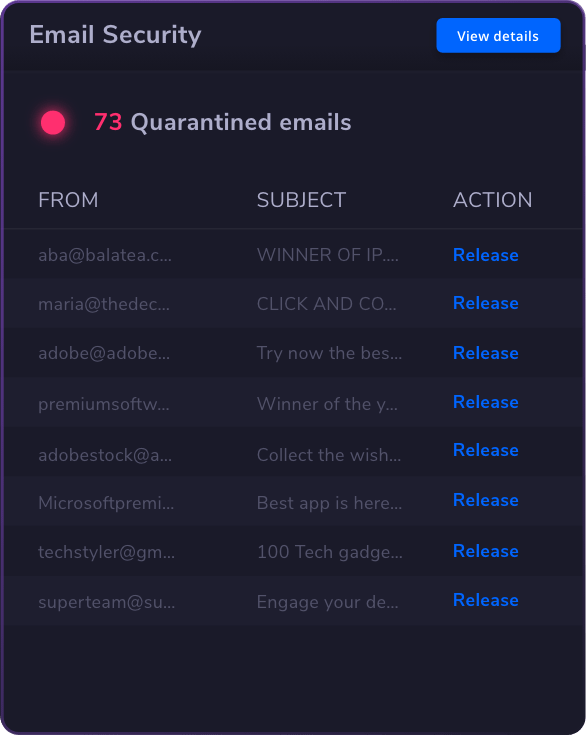
 Email & Collaboration Security
Email & Collaboration Security