Contents:
The malicious actors behind the Dridex malware strain seem to be going out of their way to prove authorities that their takedown attempts were futile. In a new spam campaign launched this morning, cyber criminals use IKEA as bait, abusing the company’s brand reputation to deceive victims. The spam email arrives with the following contents: From: [DoNotReply@ikea.com] Subject Line: Thank you for your order Contents: (see attached screenshot) Attached: IKEA receipt 607656390.doc The contents of the receipt are designed to look very trustworthy and they could fool even savvy Internet users. 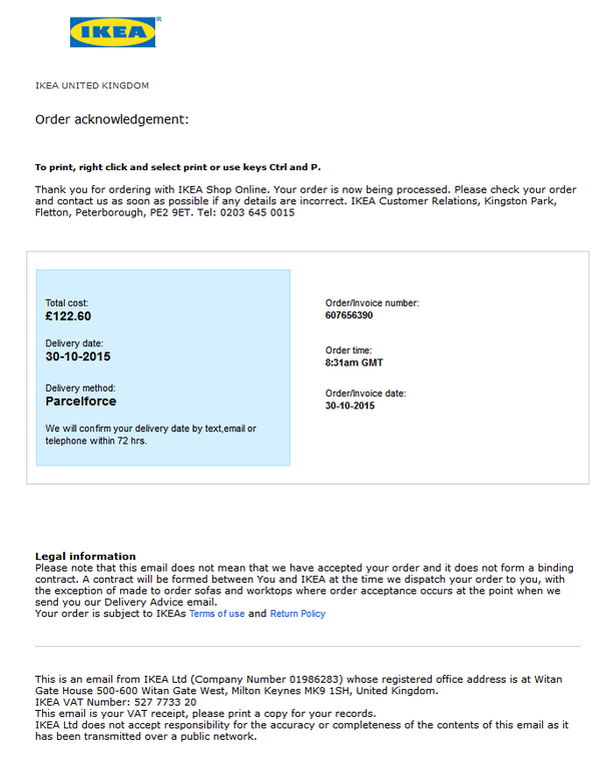 A suspicious reader would be tipped off that this could be a malicious spam email and ignore it. But to the multitasking user, who is constantly aiming to get more things done in less time, this email may not trigger any security warnings. Associating this deceiving email address with a malicious sender is possible if email servers are not configured to respect cyber security best practices.
A suspicious reader would be tipped off that this could be a malicious spam email and ignore it. But to the multitasking user, who is constantly aiming to get more things done in less time, this email may not trigger any security warnings. Associating this deceiving email address with a malicious sender is possible if email servers are not configured to respect cyber security best practices.
How the Dridex infection happens
If the recipient downloads and opens the attached document, enabling macros, the following steps will trigger the infection:
- A macro payload is activated;
- The payload will download and run Dridex, the notorious data-stealing strain from the financial Trojans category;
- Once the system is infected, Dridex attackers can start to harvest banking credentials (usernames, passwords, credit card details) and other personal information and system information to gain access to financial records and online banking accounts.
The primary target of this spam campaign are banks in Europe. The malicious payload will download Dridex from a series of compromised web pages, and it will run it on the machine with the rights of the logged-in user (sanitized by Heimdal Security): http://experassistance [.] fr / 4f67g7 / d6f7g8.exe http://alvarezsantos [.] com / 4f67g7 / d6f7g8.exe The malicious code achieves only very limited antivirus detection (3/54 on VirusTotal): 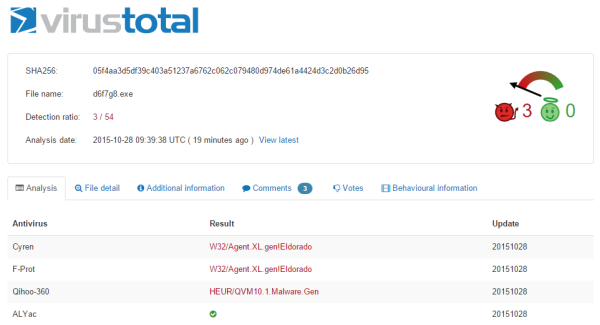 Click here for the full detection rates at the time the campaign was discovered. UPDATE: A spam run using the same tactic as described above is impersonating Booking.com to deliver data-stealing malware, including Dridex. Detection rates for it as very low as well: 4/55 on VirusTotal. The email appears as a fax message sent on behalf of Booking.com and includes an attached Word document. Once downloaded and opened, the document will require to enable macros. By doing this, the unsuspecting user will start the infection, enabling the payload to download financial and data-stealing malware. Additional details can be found in this blogpost on MyOnlineSecurity.co.uk. Cyber criminals can gain an unfair advantage by using email spoofing, a technique that allows them to forge email addresses and make them look legitimate. This tactic is not only used in spam campaigns, but in phishing and spear phishing attacks as well.
Click here for the full detection rates at the time the campaign was discovered. UPDATE: A spam run using the same tactic as described above is impersonating Booking.com to deliver data-stealing malware, including Dridex. Detection rates for it as very low as well: 4/55 on VirusTotal. The email appears as a fax message sent on behalf of Booking.com and includes an attached Word document. Once downloaded and opened, the document will require to enable macros. By doing this, the unsuspecting user will start the infection, enabling the payload to download financial and data-stealing malware. Additional details can be found in this blogpost on MyOnlineSecurity.co.uk. Cyber criminals can gain an unfair advantage by using email spoofing, a technique that allows them to forge email addresses and make them look legitimate. This tactic is not only used in spam campaigns, but in phishing and spear phishing attacks as well.
5 key facts about Dridex
- Dridex is a malware strain that has evolved from the Cridex malware (which is based on the notorious Zeus Trojan).
- Dridex first came up in late 2014, when it spread via a spam campaign that generated up to 15000 malicious emails a day, according to Trustwave.
- The attacks mainly target UK users, but they have also spread to potential victims in other countries around Europe and beyond.
- The FBI collaborated with several cyber security institutions to take the Dridex infrastructure in mid-October, but the botnet showed signs of activity only 48h later.
- The main way that Dridex is distributed by its creators is via strong spam campaigns that impersonate trusted organizations to lure potential victims.
This is the sixth Dridex spam run we have reported in the past 4 months, with many more having been discovered by other security organizations as well. Because attackers often leverage spam campaigns to reach their victims, we have dedicated an analysis to how this happens:
How Malware Creators Use Spam to Maximize Their Impact
In this analysis, we also included a safety guide that provides actionable tips on how to avoid getting infected with financial malware via unsolicited emails. This is especially important for employees in financial institutions, who are the primary target for this spam campaign and others that resemble it in tactics and objectives. Double action is needed to ward off these type of financial threats: educating employees on cyber security best practices and making sure advice is respected, and employing adequate defenses against sophisticated financial malware that is capable of evading traditional antivirus detection.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security










