Contents:
What Is Biometric Authentication?
Biometric authentication refers to the security procedure that involves the use of unique biological characteristics of individuals such as retinas, irises, voices, facial characteristics, and fingerprints in order to verify people are who they claim to be. This process is used to control access to physical and digital resources, such as buildings, rooms, and different devices.
The word biometric is a combination of two words: bio (human) and metric (measurement). In simpler words, biometrics are any metrics related to human features which make an individual different from other individuals.
Now, although biometric systems can combine authentication and identification, there is a major difference between the two. Specifically, identification asks, “who are you?” while authentication asks, “Are you who you say you are?” Biometric identification verifies you are you based on your body measurements. Biometric authentication goes one step further and uses that information to compare you against a database and enters your information in service.
How Does the Biometric Authentication Work?
Biometric authentication works by comparing two sets of data: the first one is preset by the owner of the device, while the second one belongs to a device visitor. If the two data are nearly identical, the device knows that “visitor” and “owner” are one and the same, and gives access to the person.
The important thing to note is that the match between the two data sets has to be nearly identical but not exactly identical. This is because it’s close to impossible for 2 biometric data to match 100%. For instance, you might have a slightly sweaty finger or a tiny, tiny scar that changes the print pattern.
Designing the process so that it doesn’t require an exact match greatly diminishes the chance of a false negative (the device doesn’t recognize your fingerprint) but also increases the odds that a fake fingerprint might be considered genuine.
Here’s what we will cover in this extensive explanation of biometric authentication, a fascinating technology with significant adoption in the present and huge potential in the future.
Table of contents
- Biometric Authentication Methods
- Advantages and Disadvantages of Biometric Authentication
- Biometric Authentication Use Cases
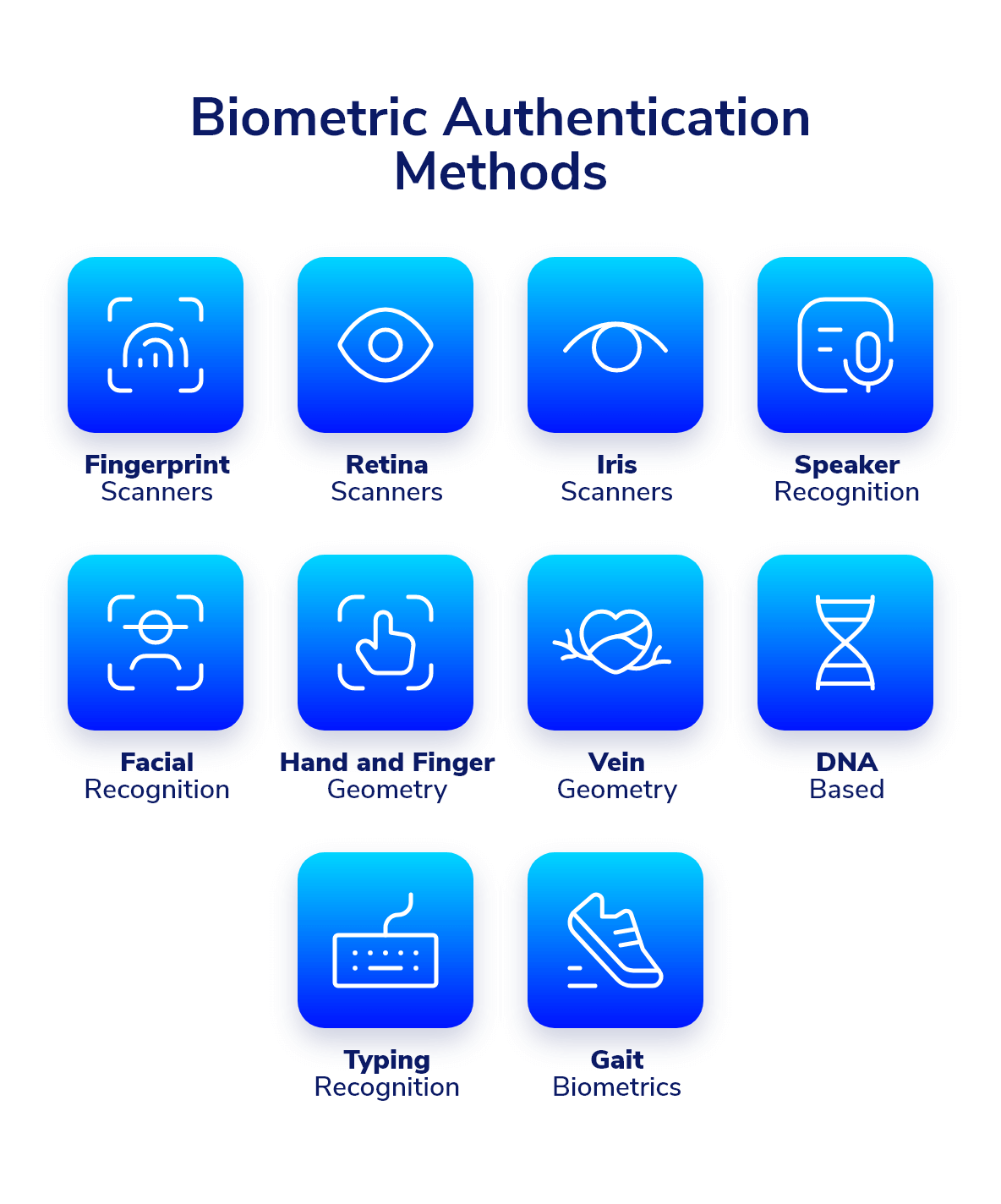
Biometric Authentication Methods
There are quite a few types of identifying a user by way of his own body. Below are the most popular biometric technologies that have made their way into users’ hands.
1. Fingerprint Scanners
There are three types of fingerprint scanners: optical, capacitive, and ultrasound.
- An optical scanner takes a photo of the finger, identifies the print pattern, and then compiles it into an identification code.
- A capacitive scanner works by measuring electrical signals sent from the finger to the scanner. Print ridges directly touch the scanner, sending electrical current, while the valleys between print ridges create air gaps. A capacitive scanner basically maps out these contact points and air gaps, resulting in an absolutely unique pattern. These are the ones used in smartphones and laptops.
- Ultrasonic scanners will make their appearance in the newest generation of smartphones. Basically, these will emit ultrasounds that will reflect back into the scanner. Similar to a capacitive one, it forms a map of the finger unique to the individual.
Creating a Fake Finger (Spoofing the Fingerprint)
To open up a smartphone secured with a fingerprint, the attacker will first need to find a high-quality print, that contains a sufficient amount of specific patterns to open up the device. Next, an attacker will lift the fingerprint, place it on a plastic laminate, and then cast a finger to fit this mold.
Once the malicious hacker creates the fake finger, all he has to do is to place it on the scanner, press with his finger to conduct electricity, and then use the unlocked phone.
2. Retina Scanners
Security researchers consider the eye as one of the most reliable body parts for biometric authentication since the retina and iris remain almost completely unchanged during a person’s lifetime. A retinal scan will illuminate the complex blood vessels in a person’s eye using infrared light, making them more visible than the surrounding tissue. Just like fingerprints, no two persons will ever have the same retinal pattern.
3. Iris Scanners
Iris scanners rely on high-quality photos or videos of one or both irises of a person. Irises too are unique to the individual. However, iris scanners have proven to be easy to trick simply by using a high-quality photograph of the subject’s eyes or face. When it comes to biometrics, the iris has several major advantages compared to a fingerprint:
- You don’t spread the information around every time you touch something.
- The iris stays virtually unchanged throughout a person’s life. A fingerprint, on the other hand, can be dirtied, scarred, or eroded.
- You can’t use a fingerprint with dirty or sweaty hands. Irises, however, have no such problem.
The only major disadvantage of an iris scanner is that high-quality photos of your face or eyes can trick the scanner and unlock the device.
Despite these limitations, the technology has made its way as a security feature in airports, banks, and other sensitive buildings. Of course, just like with other security measures, it’s used in conjunction with multiple authentication technologies.
How it works. In the enrollment phase, the scanner will take a photograph of your iris using both normal light, as well as infrared light to capture details that wouldn’t be visible otherwise.
After the device records the person’s iris, it will remove any unnecessary details, such as eyelashes, and then transform the information into mathematical data and encrypt it.
During verification, an iris scanner will again emit infrared light to spot those hidden details. Because an iris scanner supplies its own light, it also works in low light or dark conditions.
Tricking an Iris Scanner. For some iris scanners, all it takes is taking a photo with a cheap camera in night mode, print the iris on paper, and then putting a wet contact lens to mimic the roundness of the human eye.
4. Speaker Recognition
Speaker recognition, unlike voice recognition, wants to identify who is talking, and not what is being said.
In order to identify the speaker, the specialized software will break down their words into packets of frequencies called formants. These packets of formants also include a user’s tone, and together they form his voiceprint.
Speaker recognition technology is either:
- Text-dependent, meaning it unlocks after identifying certain words or phrases (think “Hey Alexa!” for the Amazon Echo).
- Text-independent, where it tries to recognize the voice itself but ignores what is actually said.
Unlike other methods mentioned here, speaker recognition comes with a significant usability problem, since it’s easy for background noises to distort the person’s voice and make it unrecognizable.
When it comes to consumer devices, voice activation can come across as awkward (a.k.a. talking to Siri in the subway).
But the biggest issue with speech recognition is how easy it is to create a high-quality reproduction of a person’s voice. Even low-quality smartphones can accurately record a person’s voice, complete with inflections, tone, and accents.
This hasn’t stopped speaker recognition and similar technologies from gaining mainstream adoption. Just look at the success of Amazon Echo, Google Home, and other voice-controlled speakers integrated into a lot of smart homes. It’s an amazing biometric authentication experience for users. At the same time, it’s a security risk of nightmare proportions.
5. Facial Recognition Systems
Generally speaking, facial recognition systems approach biometric authentication from a lot of angles.
The classic way is to simply extract your face’s features from an image (eyes, nose, distance between your lips and your nose, etc) and compare them to other images to find a match.
Through skin texture analysis, your unique lines, beauty marks, wrinkles, and so on are turned into a mathematical space, which is then compared to other images.
Both of them can be easily fooled with makeup, masks, or, in some cases, simply obstructing part of your face. This is where thermal imagery and other technologies stepped up the game until we got to this point – that of widespread adoption of systems like the Apple FaceID.
6. Hand and Finger Geometry
While not as unique as prints, iris scanners, or tridimensional face maps, our hands are different enough from other people’s. That makes them a viable authentication method in certain cases.
A hand geometry scanner will measure palm thickness, finger length and width, knuckle distance, and so on.
Advantages of this kind of system are cheapness, ease of use, and unobtrusiveness. It also has a few major disadvantages. A hand’s size can vary over time. Health problems might limit movements. More importantly, a hand is not that unique, so the system has low accuracy.
7. Vein Geometry
Our vein layout is completely unique and not even twins have the same vein geometry. In fact, the overall layout is different from one hand to another.
Veins have an added advantage since they are incredibly difficult to copy and steal because they are visible under tightly controlled circumstances.
A vein geometry scanner will light up the veins with near-infrared light, which makes your veins visible in the picture.
8.DNA Based
Deoxyribonucleic acid (DNA) is the most reliable personal identification method. It is intrinsically digital and does not modify during a person’s life. Since DNA is the structure that defines who we are physically and intellectually, it is not possible that any other human being will have the same set of genes. Of course, this does not apply to identical twins.
Nevertheless, DNA biometrics is not an infallible method of identification. If forensic experts do not carry out a DNA test properly, an individual’s identification code can be altered.
9. Behavioral identifiers (Typing Recognition and Gait Biometrics)
Typing recognition determines a person’s identity based on their unique typing characteristics such as the speed at which someone types, the length of time it takes to go from one letter to another, or the level of impact on the keyboard.
Gait recognition is a type of behavioral biometric authentication that recognizes and verifies people by their walking style and pace. Compared to other first-generation biometric modalities such as fingerprint and iris recognition, gait has the advantage of being unobtrusive, in that it requires no subject contact.
Advantages and Disadvantages of Biometric Authentication
Ultimately, biometric authentication techniques are all about security. As a feature, their main competitor is the password (or PIN code, on occasion), so a comparison between the two will reveal both their flaws and weaknesses. Let’s see.
Advantages:
- Ease of use. A fingerprint or iris scan is much easier to use than a password, especially a long one. It only takes a second (if that) for the most modern smartphones to recognize a fingerprint and allow a user to access the phone. Ultrasound scanners will soon become commonplace, since manufacturers can place them directly behind the screen, without taking any extra real estate on a phone. Voice recognition, on the other hand, is a bit iffier and background noises can easily scramble the process and render it inoperable.
- The malicious hacker has to be near you. The biggest advantage of biometrics is that a malicious hacker has to be in your physical proximity in order to collect the information required to bypass the login. This narrows down the circle of possible suspects in case your biometric lock is somehow bypassed. The proximity also puts him at risk of getting caught red-handed, in a way that regular malicious hackers working from another continent cannot.
- Biometrics are difficult to fake or steal. Biometrics such as facial recognition, fingerprint or retina scanning, and others are almost impossible to reproduce using the current technology. There’s a one in 64 billion chance that your fingerprint will correspond exactly with someone else’s.
Disadvantages:
- You cannot revoke the fingerprint/iris/voice remotely. A big disadvantage of biometric security is that a user cannot remotely alter them. If you lose access to an email, you can always initiate a remote recovery to help you regain control. During the process, you will be able to change your password or add two-factor authentication to double your account’s security. Biometrics, however, don’t work like that. You have to be physically near the device to change its initial, secure data set.
A thief could steal your smartphone, create a fake finger, and then use it to unlock the phone at will. Unless you quickly lock your phone remotely, a thief would quickly steal every bit of information on the device.
- “Master fingerprints” can trick many phones and scanners. When you first register a fingerprint, the device will ask you for multiple presses from different angles. These samples will then be used as the original data set to compare with subsequent unlock attempts. However, smartphone sensors are small, so they often rely on partial matches of fingerprints. Researchers have discovered that a set of 5 “master fingerprints” can exploit these partial matches, and open about 65% of devices. The number is likely to go down in real-life conditions, but an open rate of even 10% to 15% is huge and can expose millions of devices.
- Biometrics last a lifetime. You can always change your password if somebody learns it, but there’s no way to modify your iris, retina or fingerprint. Once somebody has a working copy of these, there’s not much you can do to stay safe, other than switching to passwords or using another finger. In one of the biggest hacks ever, the US Office of Personnel Management leaked 5.6 million employee fingerprints. For the people involved, a part of their identity will always be compromised. In CPO Magazine, we explored even more risks of using biometric data, especially in the context of law enforcement.
- Vulnerabilities in biometric authentication software A couple of years ago, security researchers discovered weaknesses in Android devices that allowed them to remotely extract a user’s fingerprint, use backdoors in the software to hijack mobile payments or even install malware. What’s more, they were able to do this remotely, without having physical access to the device.
Since then, patches have come for vulnerabilities, but bug hunters are constantly on the hunt for new ones.
Biometric Authentication Use Cases
Biometric authentication is used in almost every industry – from the financial sector and health care to retail, or travel. Due to the continuously growing instances of account takeover fraud, organizations need safe authentication and identification procedures more than ever.
Below you can find some examples of how these businesses are employing the use of biometrics to enhance the security and efficiency of existing processes.
Banking and Financial Sector
Security and authentication are vital in multiple industries, but especially in the financial sector. Financial institutions and banking organizations are integrating biometric authentication in their everyday operations to perform customer identification and for more rapid processing of user information.
According to a research conducted by Cision PR Newswire, almost 50% of the most appreciated mobile banking applications use biometric authentication.
Healthcare Sector
Healthcare facilities use biometric services to verify the identity of patients, keep a record so that whenever a person comes to the hospital his medical records could be easily and rapidly accessed by their doctor, keep sensitive data secure and prevent mix-ups.
The stored information can be used to make sure patients receive the care they need, whether that means faster identification in emergency cases, better medical diagnosis, or averting medical mistakes.
Academic Sector
Biometric authentication can also be used in school management systems where keeping records of students’ and teachers’ attendance is an ordinary custom. It is beneficial because it also keeps evidence of students’ arrival and leaving time from school, and work hours for teachers. Automated record-keeping of student identities significantly improves educational activities.
Travel and Hospitality Sector
Exclusive airlines and airports are giving their customers the possibility to check into their flight using facial recognition. In the same way, hotels and hospitality businesses are starting to allow self-check-in using biometric authentication.
Businesses Around the World Use Biometric Services
Disney’s biometric fingerprint scanners. Disney has implemented fingerprint biometrics as part of its access system since 2013. Disneyland and Walt Disney World’s entry gates require all customers who are older than 3 to scan their entry tickets and place their fingers onto a scanner to verify identification.
Barclays biometric technology. Barclays was one of the first to develop one-touch fingerprint banking access and have since expanded their biometric approach to include voice-enabled biometrics. This system allows the financial institution contact center to identify customers from the first few spoken words.
Their voice recognition technology analyses each client’s unique voice to immediately check their identity, providing Barclays with a streamlined method of authorization, whilst creating a more powerful barrier of protection against fraudulent calls.
American Airlines facial recognition biometrics. American Airlines is one of the major airline companies successfully using biometric technology in the U.S. by creating a biometric facial recognition program that plans to streamline a client’s journey through the boarding process.
Wrapping up…
Biometric authentication has strongly expanded in the last few years, with more and more consumers relying on it and even demanding it.
Over the years, we have witnessed a rising increase of organizations transitioning from traditional forms of cyber protection and access control to biometric technology.
This kind of technology provides managers the freedom to simplify their authentication process and due to the physical attributes involved in identifying employees, biometric technology offers a stronger, more advanced level of security, access control, and management over traditional counterparts.
Do you use any sort of biometric technology? How do you feel about it, especially in the government’s hands, and how secure do you think is?
This article was initially published by Ana Dascalescu in July 2017 and rewritten in July 2021 by Antonia Din.


 Network Security
Network Security
 Vulnerability Management
Vulnerability Management
 Privileged Access Management
Privileged Access Management
 Endpoint Security
Endpoint Security
 Threat Hunting
Threat Hunting
 Unified Endpoint Management
Unified Endpoint Management
 Email & Collaboration Security
Email & Collaboration Security











Great blog. Anyone interested in learning more about biometric authentication can read this blog. An example of biometric technology that allows customers to access online services using images of their fingerprints is fingerprint authentication or scanning.
Hi,
Great article.
You mention that the bio-metric scanned data is converted to a mathematical expression and encrypted. But there is little detail provided on this feature, I think that your readers should have a greater appreciation for what this actually means.
Passwords are put through a unidirectional encryption, the encrypted result is stored and each time a password is entered the encryption process is applied then only when the new encrypted password result matches the stored result matches will the device be unlocked.
Your article does not clarify if the encrypted bio-metric data is stored in a recoverable or non recoverable form, it should be no different then passwords, but that is not to say that all devices adopt this principle of unidirectional encryption.
Firstly I would like to thanks the authors (cybersecurity experts) for this interesting article. It is true that there are loads of advantages an disadvantages of using biometric authentication as another security factor, but most of the disadvantages mentioned in the post could be solved by using a multi-biometric authentication solution adding extra security layers to the process and choosing the best method regarding the environmental conditions.
Anyway, If you are interested in learning more about benefits derived of using biometric authentication you can do it here: https://www.mobbeel.com/en/blog/benefits-derived-from-the-biometric-authentication/
Biometrics, since it first became a concept from movies, have become a reality. Its cool how security have evolved to make sure that our personal uniqueness are truly are own and the only way to access our personal data. Great article!
Bio-metric authentication is going on everywhere it looks it is need of time. but everyone should be more careful about this because if a technology is very highly improved carelessness may lead to scams.
We do need more frictionless ways of authenticating with aps and websites than usernames and passwords. So voice text dependent biometrics seems the best option to me
The voice can be recorded so easily and can be reconstructed too and is a huge security risk as it is the most easily accessible commodity, especially high profile targets.
Great post! There is certainly a distinct need of innovations in security particularly in the field of authentication and Bio-metrics is surely a good example of this. Totally agreed with what you said here that Bio metrics is being used everywhere today in the form of fingerprint scanner, retina scanner or face recognition. This second layer of protection is certainly a great thing to secure your customer’s private data.
There was some challenges in Bio metrics :
We cannot alter them Remotely need Physical access all the time.
We cannot modify our Bio metrics like our Password change.
There was a possibility of morphing our Bio metrics.
Always combination of any two like Password + Key based or Key based + Bio metrics or Password + Bio metrics is more secure way for Authentication